Do not pass GO - Malicious Package Alert
2025年2月12日
0 分で読めますResearchers recently found another Software Supply Chain issue in BoltDB, a popular database tool in the Go programming environment. The BoltDB Go Module was found backdoored and contained hidden malicious code. This version took advantage of how Go manages and caches its modules, allowing it to go unnoticed for several years. This backdoor allows hackers to remotely control infected computers through a server that sends them commands i.e. via a command and control server. The harmful version (1.3.1) was released on GitHub in November 2021. After its release, the Go Module Mirror service stored it permanently.
What is a Typo Squatting attack?
Typo squatting attacks happen when bad actors create and upload harmful software packages to online libraries using names very similar to popular ones. They hope people will mistakenly download and install these dangerous versions instead of the legitimate software they thought.
Read more here - https://snyk.io/blog/typosquatting-attacks/
The malicious Go Module Mirror’s was named github.com/botdb-go/bolt, similar to the original one i.e. github.com/boltdb/bolt. The malicious package, when found, was reverted to the actual legitimate version however, Go Module Mirror’s indefinite caching of modules kicked in, and that cached the backdored module. Another point that played a big part here is that we now wish to update our systems to the latest dependencies, which led developers to update the version that stayed in the system for 3 years. Socket researchers reported the Go Module Mirror to GitHub and Google on January 30, 2025. The Module was cached on Go Module Proxy, which continued to serve clients.
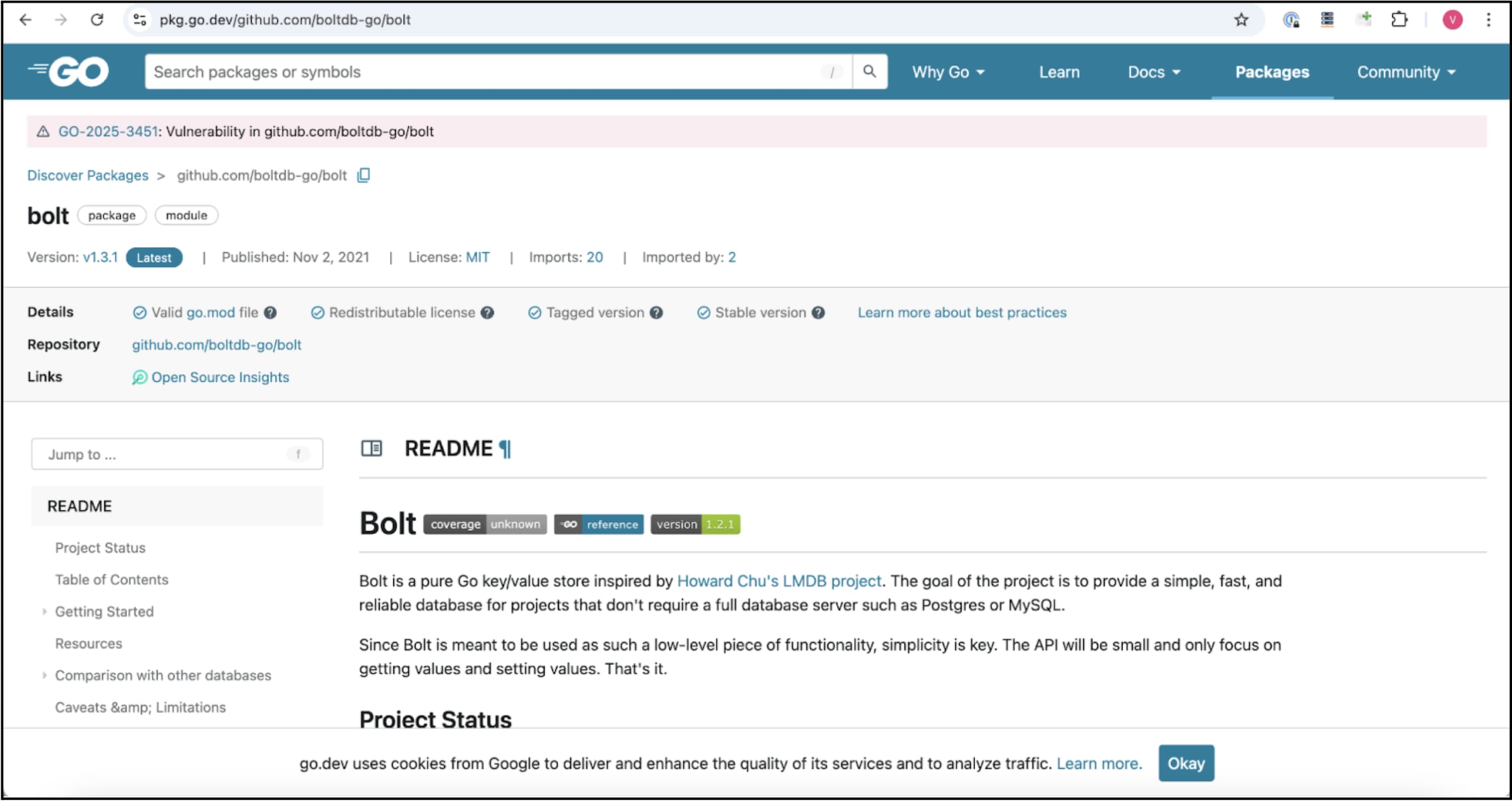
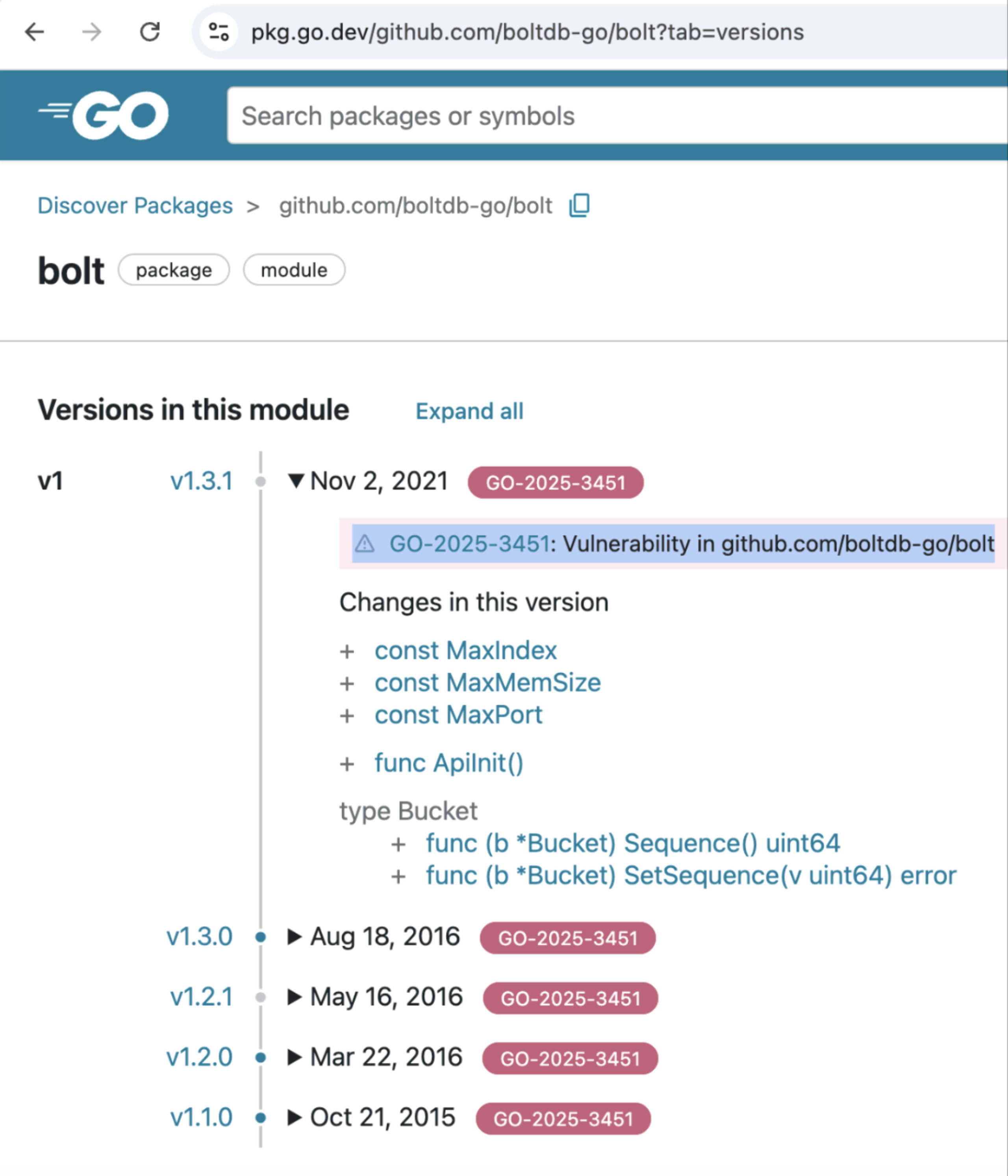
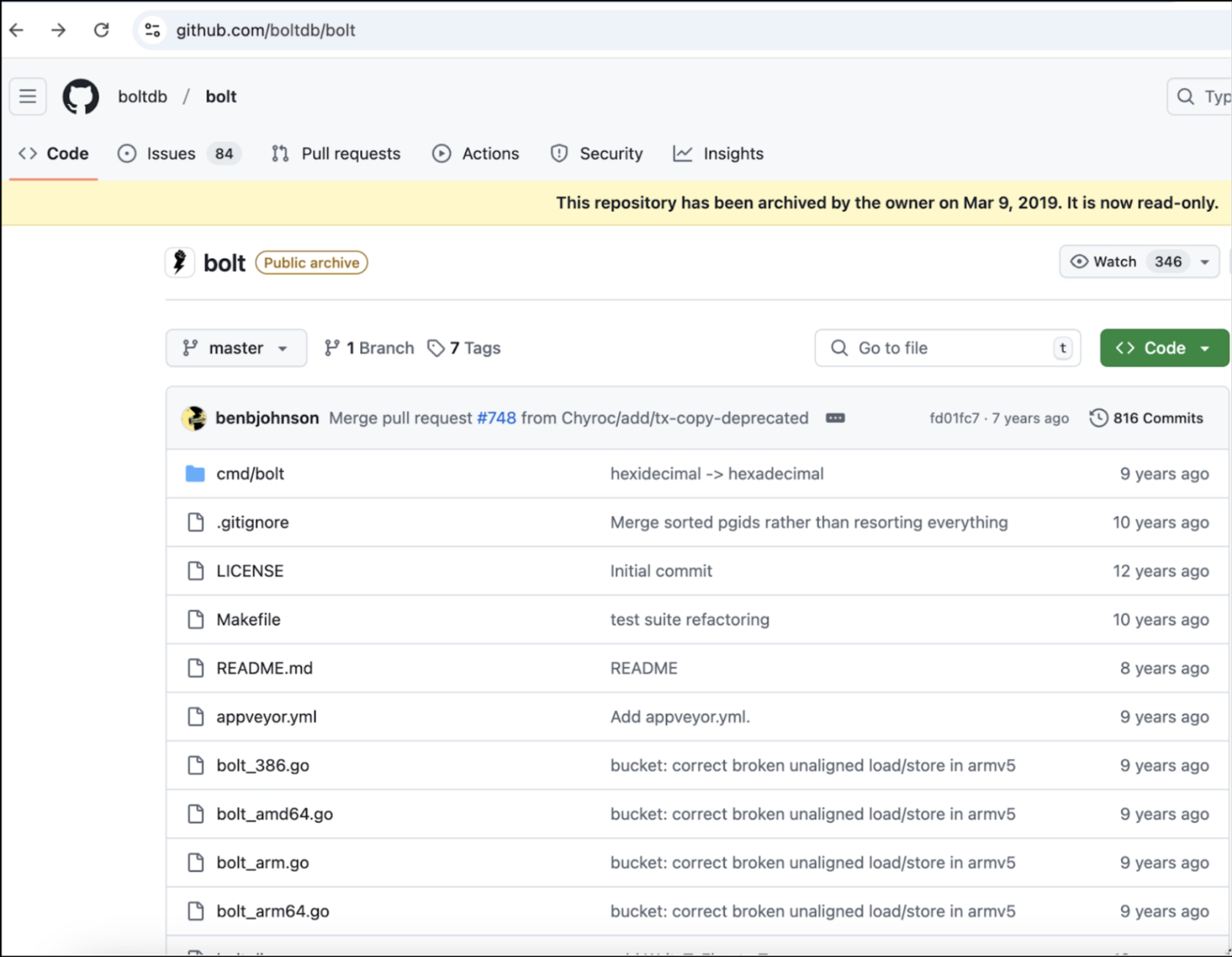
There have been over 80+ unresolved issues in the original repository since 2015.
Impact
Impacted thousands of organizations for over three years
A big flaw in the supply chain ecosystem
Malicious packages can still be searchable on Go Module Proxy
Action Taken
As per an update from Arstechnia on February 7, 2025, a Google representative provided the following statement:
“The module has been removed from both the Go module proxy and GitHub, and we’ve added it to the Go vulnerability database for anyone who thinks they may have been impacted. We are addressing this through fixes like capability analysis via Capslock and running comparisons with deps.dev. We want to thank Socket and the Go team contributors that detected the module and are addressing fixes. We’ll continue to work with the wider industry to raise awareness around common open source security issues like these and work being done through initiatives like SLSA and OpenSSF.”
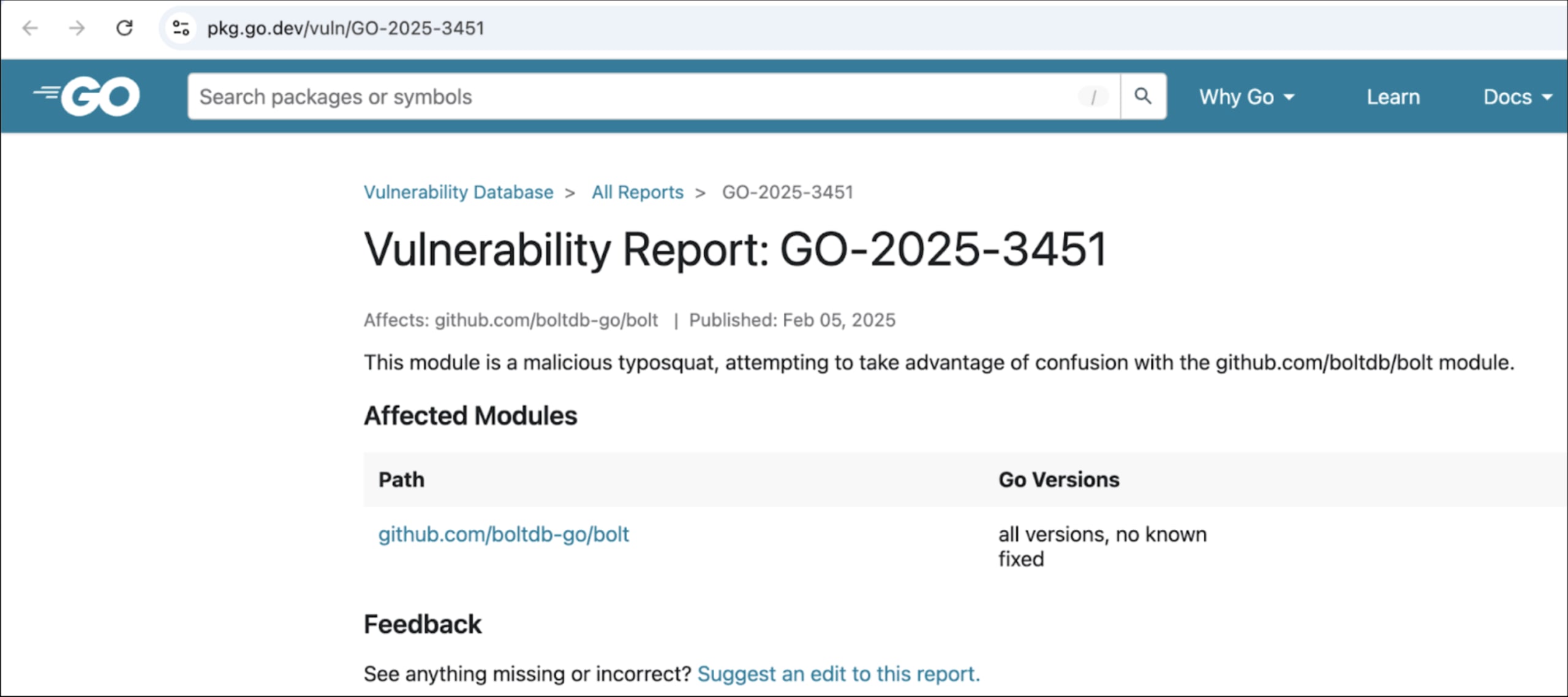
Go Module Mirror’s vulnerable package has been removed from Github.
Mitigation
Follow supply chain risks and best practices:
https://snyk.io/blog/supply-chain-risks-and-best-practices/
Checkout the 4 best practices to mitigate software supply chain attacks
https://snyk.io/articles/software-supply-chain-security/#best
Use Snyk to secure the software supply chain https://snyk.io/solutions/software-supply-chain-security/
References:
Snyk Open Source advisory: https://security.snyk.io/vuln/SNYK-GOLANG-GITHUBCOMBOLTDBGOBOLT-868841
https://socket.dev/blog/malicious-package-exploits-go-module-proxy-caching-for-persistence
https://thehackernews.com/2025/02/malicious-go-package-exploits-module.html
Play Fetch the Flag
Test your security skills in our CTF event on February 27, from 9 am - 9 pm ET.
