Detect vulnerabilities in Dockerfiles, directly from Git
Danielle Inbar
2020年11月12日
0 分で読めますWe’re pleased to announce the latest enhancement to Snyk Container—detecting Dockerfiles straight from Git repos to better empower shift-left security.
With this new capability, we now offer an easy and early scan of your Dockerfile, before you even build an image, to help shift security left and surface base image vulnerabilities, helping you choose the best base image to get your project started.
Due to the massive increase in container usage we’ve witnessed in the past few years, the importance of container security climbed as well. To get everybody on the same page and provide some background, Docker can build images automatically by reading instructions from a Dockerfile. A Dockerfile is a text document containing a set of commands needed to set up the image. The image can then run as a container.
Dockerfiles are powerful—they are simple and straightforward and can work everywhere with no specific prerequisites. Since Dockerfiles are simple text files, it seems like they’re everywhere, and they are easily shareable, which is one reason Docker is so useful to developers. But if you build on top of a base image that is old or full of vulnerabilities, you can make it difficult to fix those issues later when changes might break your application.
Dive into your Dockerfile
Auto-detecting Dockerfiles from your source code repository aligns well with our goal to make container security easier for developers and makes the Dockerfile a first-class citizen in Snyk. Up until now, you could manually attach a Dockerfile to an image scanned Snyk, but this forced you to first build the image, and then work backwards to attach the Dockerfile and check for security issues. Now, we can separate the two and enable you to get insights on your Dockerfiles at an earlier phase.
With the new capability, all you need is to import your Git repositories into Snyk, and we will automatically identify Dockerfiles, for which we provide you with enhanced visibility into security issues in your base image. In the image below, you can see the results of scanning a Dockerfile imported from a GitHub repository. From the Dockerfile we can determine the node:10.8.0-jessie parent image and provide details on the contents and vulnerabilities present in that base image, including relevant details like exploit maturity.
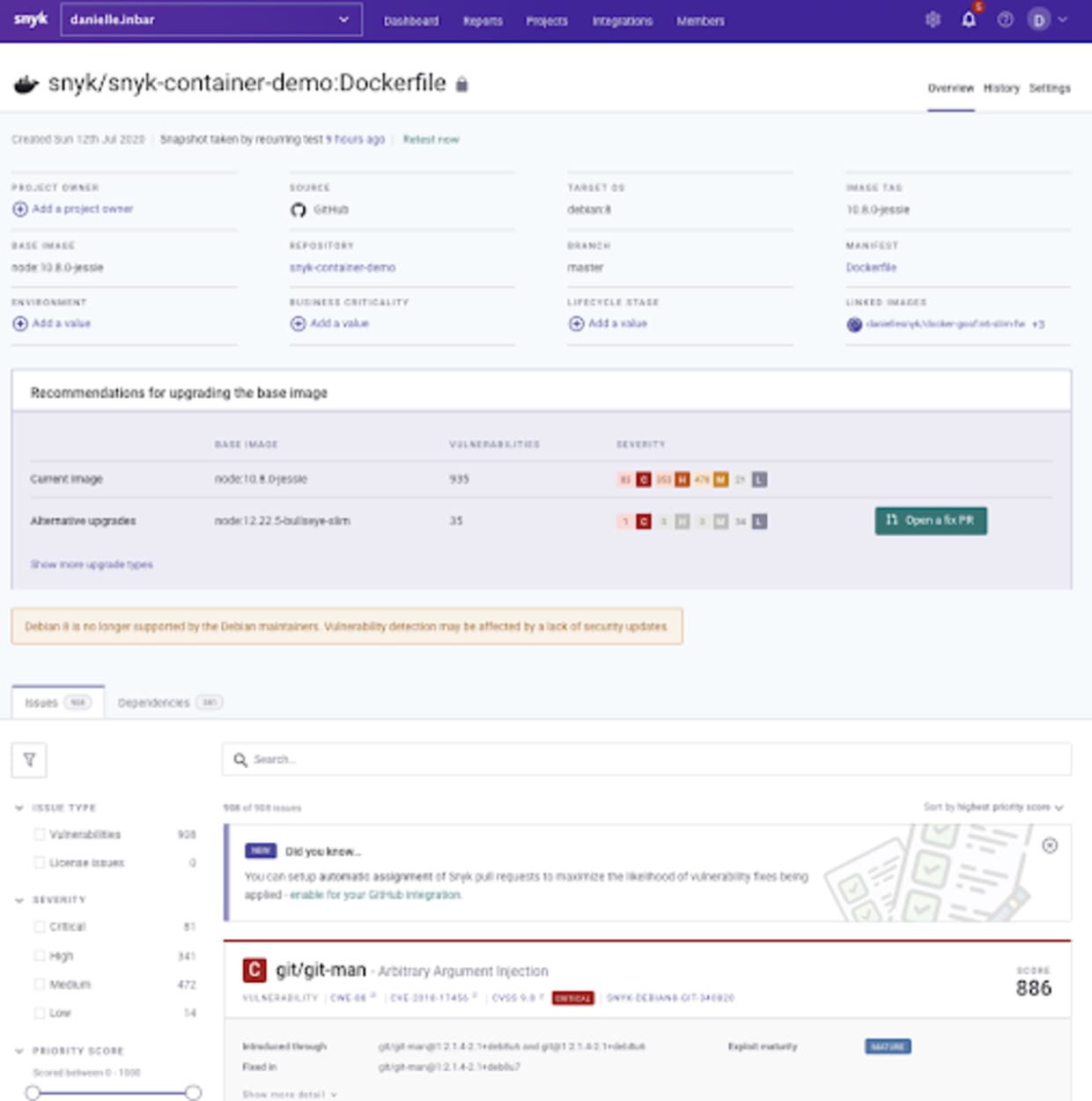
Easily maintain an up-to-date base image
We know it’s not easy to keep your base images up-to-date but worry not, because we just made it much simpler. Once a Dockerfile is detected, we look at the base image being used as part of it. On top of surfacing its vulnerabilities, Snyk also checks whether there are other, less vulnerable, base images that can suit your needs. We then raise those alternative suggestions as recommendations for you to use, to decrease exposure to vulnerabilities, and keep an up-to-date base image—as seen in the example below:
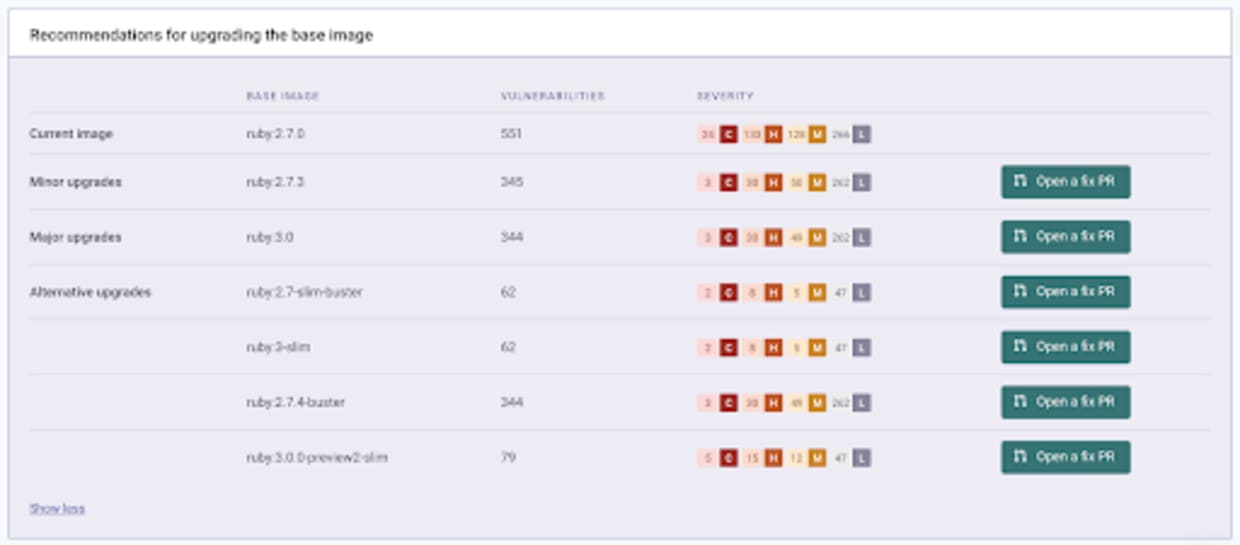
Dockerfile and image linking
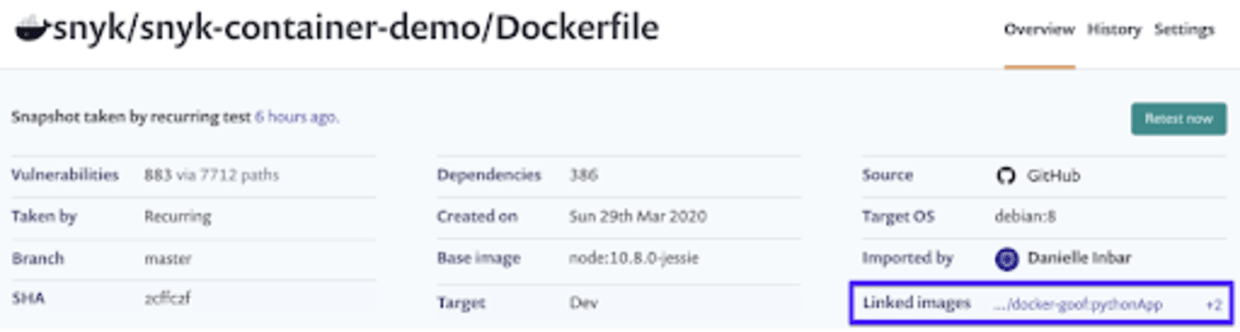
The new capability comes with a number of unique features, meant to help you understand the effect of Dockerfile issues across your projects. One important feature is the ability to link between a Dockerfile to all container images built from it. This can be used to get a sense of the security impact on your running applications and understand which images can be better secured in case you decide to take action and update your Dockerfile base image. This can also help in logically organizing connections between your images and what set of commands was used to build them. Maintaining a link between a Dockerfile and the images created from it has been a challenge for users for a while and this new feature helps solve that issue and improve your container hygiene.
To wrap things up
As you probably noticed by now, with Snyk Container it becomes quite easy to scan and detect issues in your Dockerfiles. Moreover, you can actually benefit from it immediately, by checking out the base image recommendations we provide and use it to fix issues before even building images. The new capability is available in Snyk today and is supported in all the Git integrations we have today, whether it’s on-prem or cloud-based:
Azure repos
GitHub
GitLab
Bitbucket Server
Bitbucket Cloud
GitHub Enterprise Server
For more information, more details are provided in our documentation.
Let us know what you think
We’re always working to improve Snyk on all its integrations and appreciate constant feedback. Please let us know what you think, and if there is anything specific you’d like to see next.
開発者ファーストのコンテナセキュリティ
Snyk は、コンテナイメージと Kubernetes ワークロードの脆弱性を検出して、自動的に修正します。
