Four easy ways to analyze your Java and Kotlin code
2024年8月13日
0 分で読めますNowadays, the security of your applications is just as important as the functionality they provide. Therefore, analyzing your code for security vulnerabilities is a vital part of maintaining the integrity of your applications and protecting your users' data. As developers, we are at the front lines of this battle. It's our responsibility to ensure that the code we write is not just functional and efficient but also secure.
Static Application Security Testing (SAST) is a method to discover security vulnerabilities in application code. It works by analyzing an application's source code or bytecode, looking for security flaws and other issues that could lead to security breaches. Snyk Code is a great tool for this kind of analysis, allowing developers to quickly and easily spot potential vulnerabilities and fix them before they become a problem.
Neglecting SAST tools like Snyk Code in your development lifecycle can have significant consequences. Waiting until the later stages of the development cycle to address security issues can be costly and time-consuming. More importantly, it can also lead to vulnerabilities being missed and making their way into the final product. By adopting a proactive approach to security and making SAST a part of your regular development process, you can save time and money and potentially avoid a damaging security breach.
Utilizing Snyk Code for Java projects
Snyk is a variety of security tools focused on developers that help you find and fix vulnerabilities in your source code, open source packages, container images, and misconfigurations in your cloud infrastructure. One of the most powerful features of Snyk is Snyk Code, a feature specifically designed to analyze your code for security vulnerabilities. Snyk Code supports various programming languages, including Java and Kotlin, making it an ideal choice for JVM projects.
Snyk Code is a machine learning-powered SAST tool to detect potential security vulnerabilities in your code. It can identify various issues, from injection flaws to insecure deserialization. It shows the flow of the vulnerable code in your system to better understand what is happening. It even provides detailed remediation advice to help you fix these issues, effectively hardening your application security.
The extra benefit is that you are not bound to one way of working. Snyk provides you with this capability in many different forms, so you can pick the option that best suits your way of working.
Option 1: Source code scanning using the Snyk CLI
In this section, we will discuss how to analyze your Java source code for security vulnerabilities using the Snyk Command Line Interface (CLI). With the Snyk CLI, you can easily integrate Snyk's powerful security analysis capabilities into your development workflows, making it easier to identify and address vulnerabilities early in the development process.
The Snyk CLI is a command line interface for the Snyk platform. By using Snyk CLI, you can incorporate Snyk’s security analysis directly into your local development process, CI/CD pipelines, and other automation workflows.
To conduct Static Application Security Testing (SAST) with the Snyk CLI, you need to install the CLI and authenticate it with your Snyk account. Here is how you can do this:
1# Install the Snyk CLI using NPM
2npm install -g snyk
3
4# Authenticate the CLI with your Snyk account
5snyk authOnce installed and authenticated, you can use the `snyk code test` command to analyze your Java source code:
1# Navigate to your project directory
2cd /path/to/your/java/project
3
4# Scan your source code with Snyk Code
5snyk code testThis command will analyze your source code for vulnerabilities and provide a detailed report of any issues it finds.
The Snyk CLI is versatile and can be used in several ways depending on your needs. For instance, if you want to scan your code each time you commit changes, you can integrate the CLI commands into your pre-commit hooks. Alternatively, you can include the CLI commands in your Continuous Integration/Continuous Deployment (CI/CD) pipelines to ensure your code is analyzed for vulnerabilities before it's deployed.
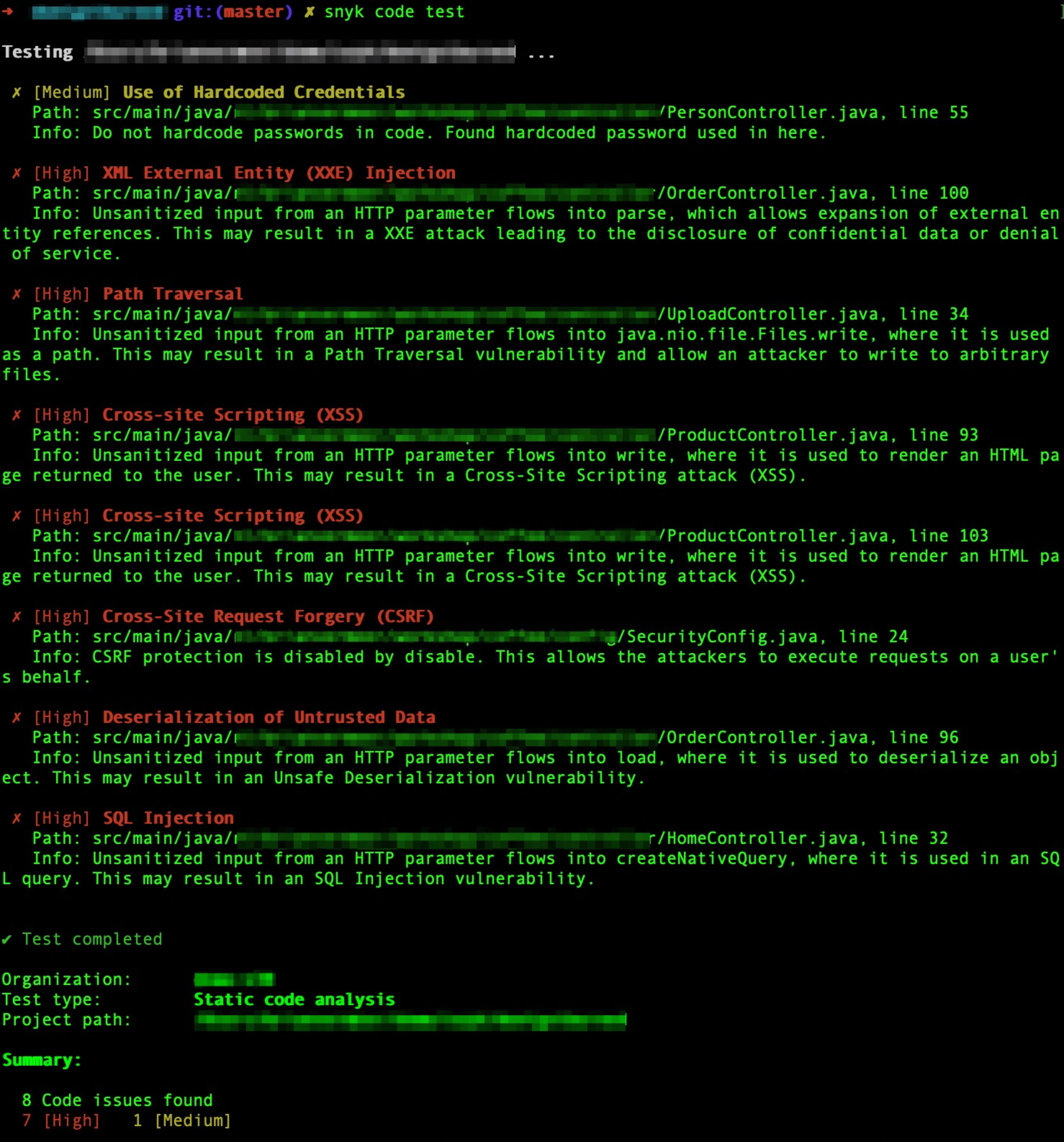
Remember, the earlier you find and fix security vulnerabilities, the safer your application will be. So why not start on your local machine before even committing the code? All you have to do is create a (free) Snyk account and install the Snyk CLI
Don't have a Snyk account yet? Sign up for Snyk today and start securing your code.
Option 2: Using Snyk code via IDE integrations
As a developer, your Integrated Development Environment (IDE) is your primary workspace, and having security seamlessly integrated into your IDE can save you time and protect your code from vulnerabilities. Snyk provides IDE integrations for IntelliJ and Visual Studio Code, enabling you to analyze your Java code for security vulnerabilities directly from your IDE.
Snyk IntelliJ plugin
The Snyk IntelliJ plugin is a powerful tool that provides real-time feedback on your Java code's security. Once you've installed the plugin, you can scan your project by right-clicking on it and selecting Snyk, then Scan Project. The plugin will then analyze your code and provide a list of potential vulnerabilities, their severity, and even suggestions for how to fix them.
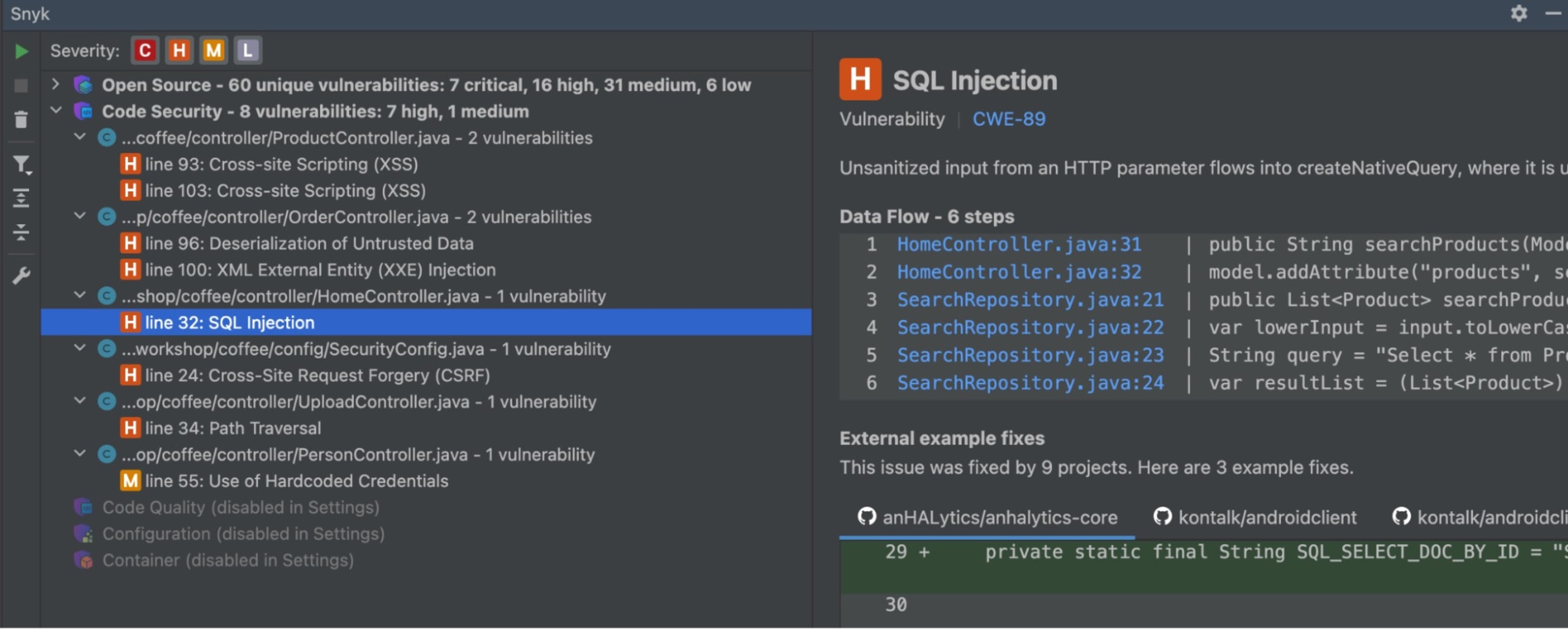
In the above example, the Snyk IntelliJ plugin would detect that the SQL query is susceptible to SQL Injection attacks.
Snyk VS Code plugin
The Snyk VS Code plugin is another excellent tool for analyzing Java code for security vulnerabilities. To use it, you need to install the Snyk extension from the VS Code marketplace. Once installed, you can right-click on your project in the Explorer view and select Scan with Snyk. The plugin will then perform a detailed analysis of your Java and Kotlin code for any recognized security vulnerabilities, providing you with a list of issues and suggested remediation steps.
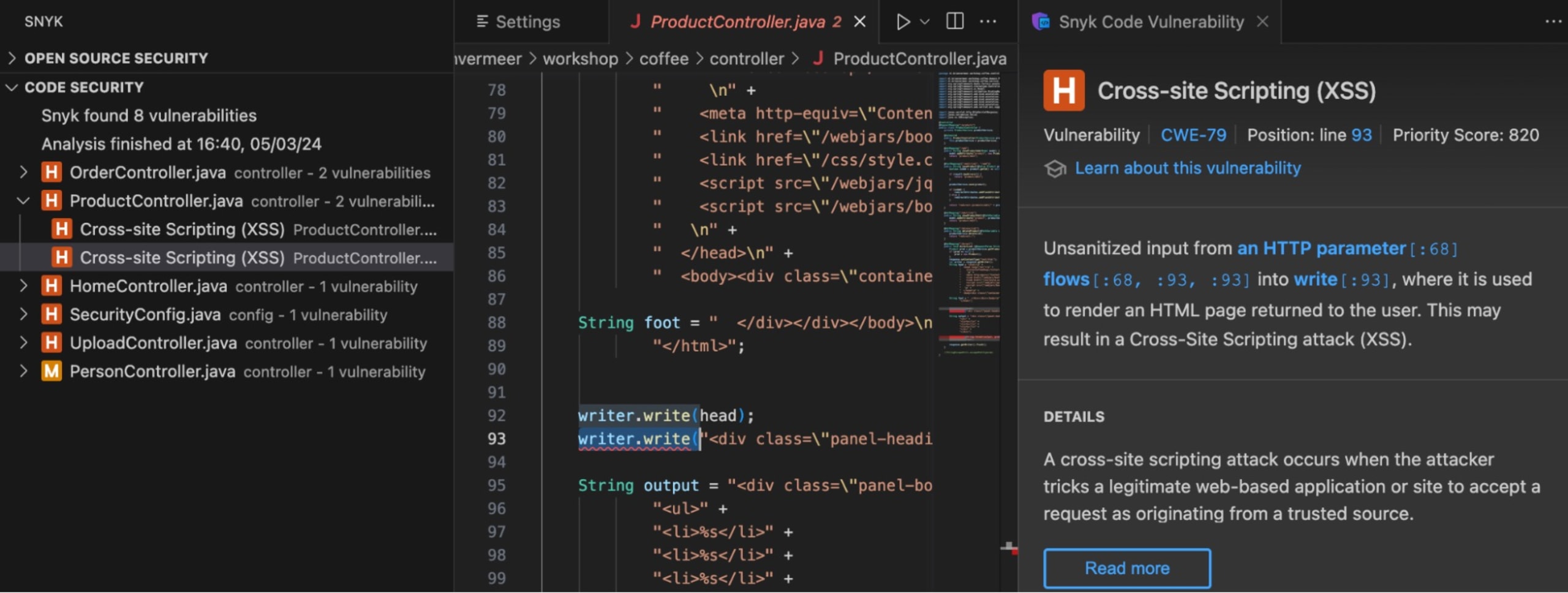
In the above example, the Snyk VS Code plugin would detect that the HTML output is vulnerable to cross-site scripting (XSS) attacks.
By integrating Snyk into your IDE, you can ensure the security of your Java code right from the start. Don't wait until deployment to consider security.
Option 3: Connect your Git repository to Snyk and enable code scanning
Connecting your Git repository to Snyk is a fundamental step in your journey to enhance Java code and application security. Thankfully, Snyk integrates seamlessly with popular source control repositories, including GitHub, GitLab, Azure Repo, and BitBucket. This integration allows your Java code to be continuously scanned for vulnerabilities, enhancing your application security.
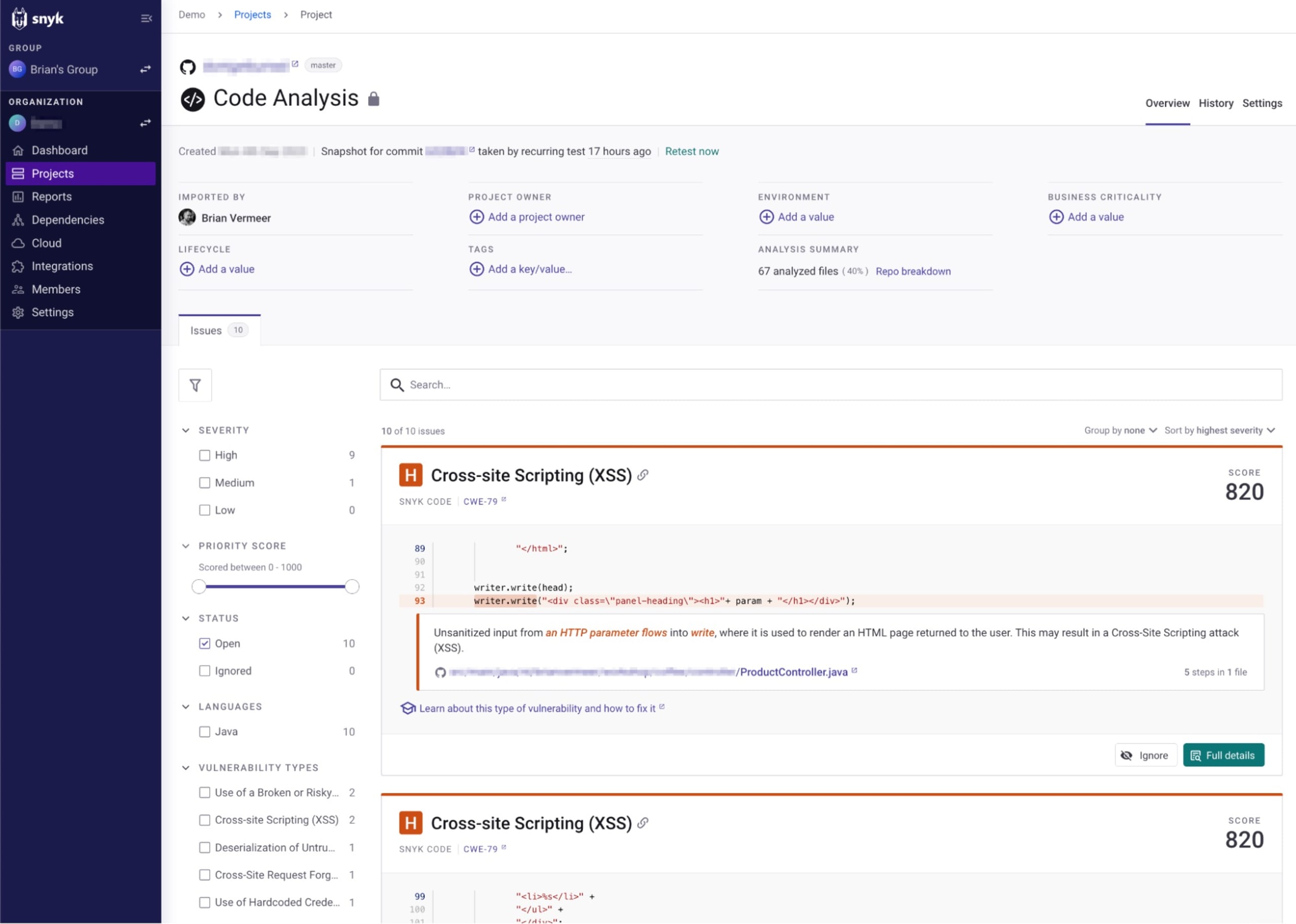
With the above Java code snippet as an example, once your Git repository is linked to Snyk, Snyk Code will automatically analyze the code using Static Application Security Testing (SAST). This analysis detects security vulnerabilities, such as SQL injection, cross-site scripting (XSS), and insecure deserialization, among others, and displays them in the Snyk User Interface (UI).
One of the unique selling points of Snyk is that it does not just identify vulnerabilities but also provides remediation advice. Through Snyk's UI, you can view the details of the identified vulnerabilities, understand their possible impact, and get advice on how to fix them. This feature sets Snyk apart from other security tools and makes it a valuable resource for developers who are keen on bolstering their application's security.
Checking pull requests for code changes that are vulnerable
Another great feature of Snyk is its ability to check pull requests for code changes that might introduce vulnerabilities. By doing this, you can catch potential security issues before they get merged into the main codebase. This preventive approach is crucial in maintaining the integrity and security of your Java application.
Option 4: Integrate with your CI pipeline and leverage Snyk Code
Integrating Snyk Code into your CI/CD pipeline is an excellent way to automate code security analysis and ensure that your Java code is free from vulnerabilities. By leveraging Snyk Code's capabilities, you can detect and fix security issues in your code before they become threats to your application's security.
In this section, we will discuss how to integrate Snyk Code into your pipeline with plugins, use GitHub actions provided by Snyk to do SAST scanning, and create a custom integration for Snyk Code using the CLI and the JSON output.
Snyk provides plugins for various CI/CD tools such as Jenkins, CircleCI, Azure Pipelines, and more. By integrating Snyk Code into your pipeline with these plugins, you can automate the process of detecting and fixing security vulnerabilities in your Java code.
Use GitHub actions provided by Snyk to do SAST scanning
Snyk also provides GitHub actions for SAST scanning. By using these actions, you can automate the process of scanning your Java code for security vulnerabilities within your GitHub repositories.
Here's an example of how you can use a GitHub action provided by Snyk to scan your Java code:
1name: Snyk
2on:
3 push:
4 branches: [ master ]
5 pull_request:
6 branches: [ master ]
7jobs:
8 security:
9 runs-on: ubuntu-latest
10 steps:
11 - name: Check out code
12 uses: actions/checkout@v2
13 - name: Run Snyk to find vulnerabilities
14 uses: snyk/actions/java@master
15 env:
16 SNYK_TOKEN: ${{ secrets.SNYK_TOKEN }}In this example, the Snyk action for Java is used to scan the Java code whenever a push or pull request is made to the master branch.
Create a custom integration for Snyk Code using the CLI and the JSON output
You can also create a custom integration for Snyk Code using the CLI and the JSON output. This can be useful if you want to customize the process of scanning your Java code for security vulnerabilities.
Here's an example of how you can do this:
1#!/bin/bash
2# Run Snyk test and output the results as JSON
3snyk test --all-projects --json > snyk_output.jsonIn this example, the Snyk CLI is used to run Snyk test, and the results are outputted as JSON. This JSON output can then be used for further processing or analysis.
By integrating Snyk Code into your CI/CD pipeline, you can ensure that your Java code is continuously scanned for security vulnerabilities, making your application security more robust.
Scan your code during all phases of development
In summary, let's emphasize a crucial takeaway for Java and Kotlin developers: the indispensable role of consistently scanning our application code throughout every phase of development. Catching issues early and frequently isn't just about fixing bugs. It's about creating a culture of quality and security from the get-go. Using a SAST tool like Snyk Code isn't just adding another gadget to our developer toolbelt. It's about establishing a basic habit in how we work, no matter how we've set things up. When we slot it into our process correctly, it feels like it's always been there, helping us catch issues without getting in the way.
As developers, we often juggle various tasks, from writing business logic to ensuring our codebase is secure and performant. Incorporating a SAST scanner that adapts to our unique ways of working — be it through IDE plugins, CI/CD pipelines, or direct git integrations — means we can make security and quality checks an intuitive part of our development process rather than a disruptive chore. This adaptability ensures that we can focus on crafting excellent Java and Kotlin applications, secure in the knowledge that our code is being continuously evaluated for vulnerabilities and anti-patterns.
Embracing a tool like Snyk Code across all cycles of development improves the quality and security of our projects. By making scanning an integral, effortless part of our development routine, we empower ourselves to catch and address issues long before they can escalate into significant concerns. So, let's champion the practice of early and frequent scans. It's a decision that pays dividends in code quality, security, and peace of mind — benefits that, as developers, we all can appreciate.
開発時にセキュリティを確保する
Snyk でコードをスキャンして品質とセキュリティの問題を検出し、IDE で修正のアドバイスを表示できます。