Yet another malicious package found in npm, targeting cryptocurrency wallets
17. Juni 2019
0 Min. LesezeitCryptocurrency wallet developer Komodo has been in the news recently as the most recent victim of an attempted cryptocurrency attack by malicious code injection via npm dependencies. The EasyDEX-GUI project which provides a graphical user interface (GUI) to SuperNET/Iguana cryptocurrency APIs and is used by Komodo’s Agama wallet has been found to contain a malicious package namedelectron-native-notify. This was disclosed via a GitHub commit against the source repo by GitHub user sawlysawly. It is estimated that there are approximately $13 million USD in cryptocurrency stored in the Agama wallets, a portion of which could have been stolen, had the npm security team not acted when they did.
We at Snyk have now added the malicious package to our vulnerability database. If your project is being monitored by Snyk and we find the malicious dependency (any version of electron-native-notify), you will be notified via Snyk’s routine alerts.
If your projects are not monitored by Snyk and you’d like to test them for the use of this package you can do so below, or by using our CLI to test your projects locally.
The timeline of events
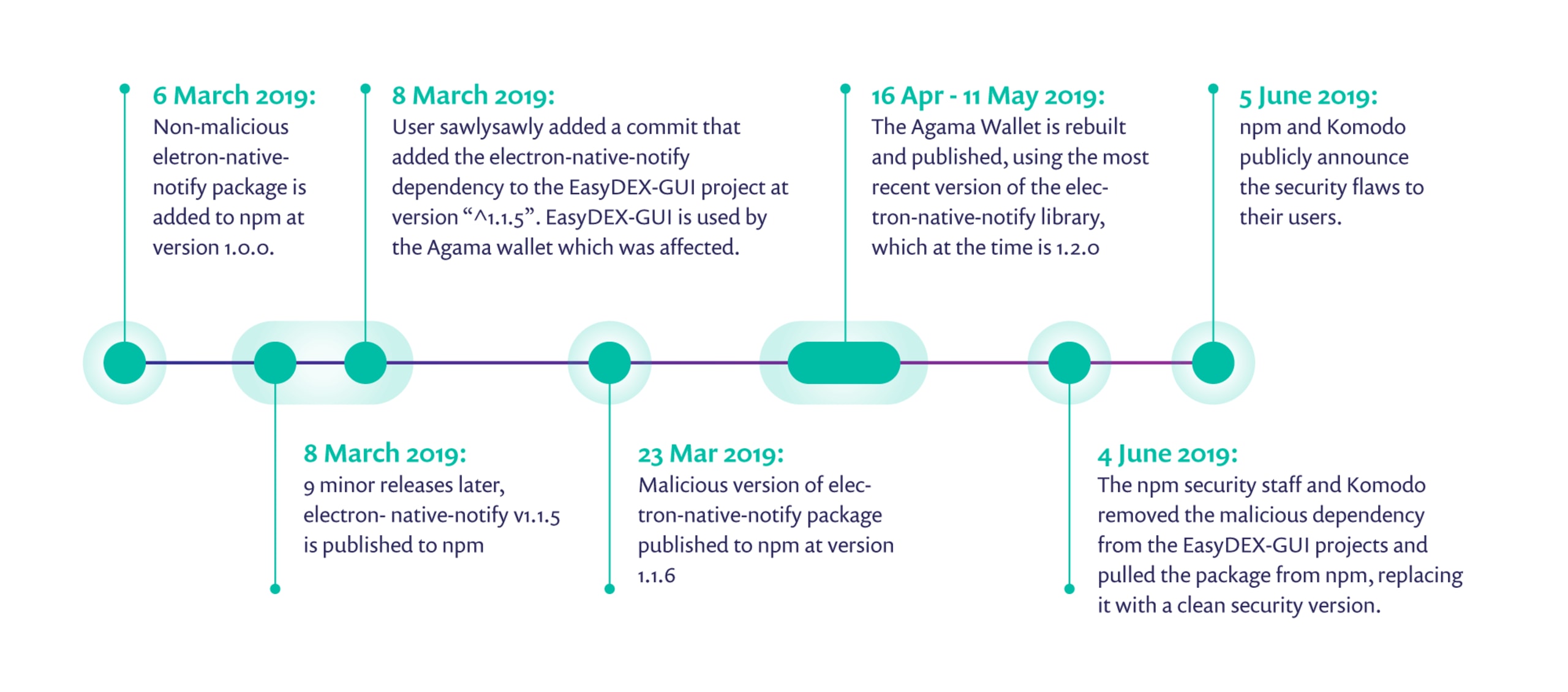
6 March 2019: Non-malicious electron-native-notify package is added to npm at version 1.0.0.
8 March 2019: 9 minor releases later, electron-native-notify v1.1.5 is published to npm
8 March 2019: User sawlysawly added a commit that added the electron-native-notify dependency to the EasyDEX-GUI project at version “^1.1.5”. EasyDEX-GUI is used by the Agama wallet which was affected.
23 Mar 2019: Malicious version of electron-native-notify package published to npm at version 1.1.6
Sometime between 16 Apr and 11 May 2019: The Agama Wallet is rebuilt and published, using the most recent version of the electron-native-notify library, which at the time is 1.2.0
4 June 2019: The npm security staff and Komodo removed the malicious dependency from the EasyDEX-GUI projects and pulled the package from npm, replacing it with a clean security version.
5 June 2019:npm and Komodo publicly announce the security flaws to their users.
The impact
The malicious code sends an HTTP GET request to a Heroku endpoint, https://updatecheck.herokuapp.com/check, reportedly downloading a payload that further executes and sends the wallet seed to the same server. The npm team created a video that shows this in action:

I’m affected, what should I do next?
Your immediate priority should be to check if you are using the malicious library in question. If so, future builds of your application will fail, but any previously deployed applications likely contain (and are potentially executing) the malicious code.
If your project is being monitored by Snyk, you will be notified via Snyk’s routine alerts should your application contain this malicious package.
If however, you are not monitoring your projects with Snyk (yet!) you can run a one-off test, using Snyk to test your repositories, or by using our CLI to test your projects locally.
If you’re a user of the Amama wallet, or you have other assets than KMD and BTC, Komodo strongly recommends moving all funds from Agama to a new address as soon as possible. They list safe wallets and provide information about moving on their support page.
Beginnen Sie mit Capture the Flag
Lernen Sie, wie Sie Capture the Flag-Herausforderungen lösen, indem Sie sich unseren virtuellen 101-Workshop auf Abruf ansehen.
