Log4Shell remediation with Snyk by the numbers
Jason Lane
5. Februar 2022
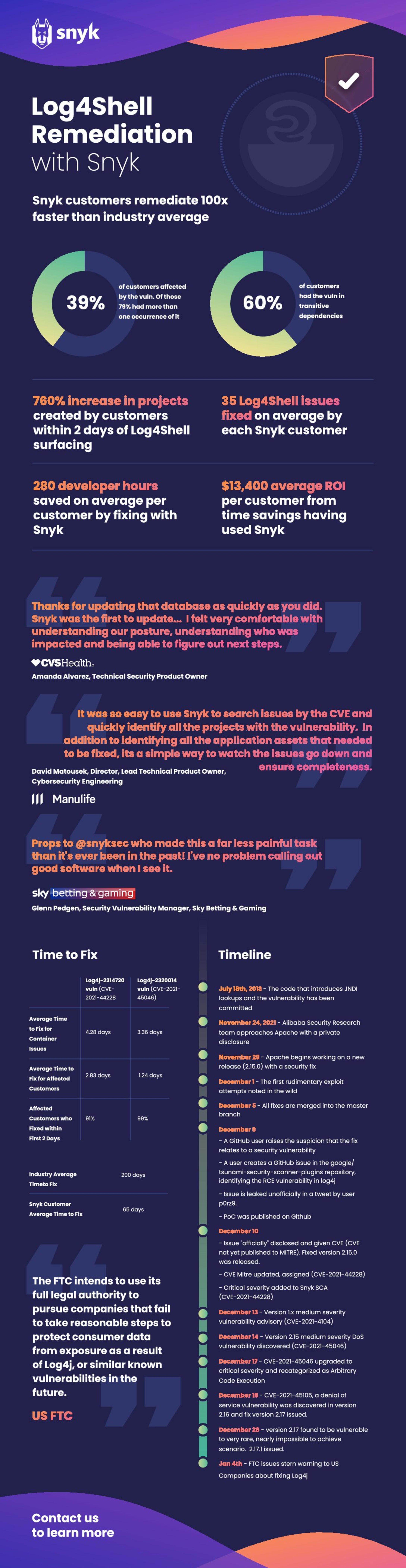
0 Min. LesezeitWe're almost two months from the disclosure of Log4Shell, and we here at Snyk couldn't be more excited with the role we've gotten to play in finding and fixing this critical vulnerability that's impacted so many Java shops. For starters, we've been able to help our customers remediate Log4Shell 100x faster than the industry average!
How have we been able to achieve that? Well, a few ways...
Getting Log4Shell into the Snyk Intel Vulnerability Database ASAP
Real-time scanning for Log4Shell in dependencies and containers
Scanning transitive dependencies (including unmanaged and shaded JARs)
Automatically creating fix PRs so teams can merge and move on
Check out this handy infographic to learn more about the Log4Shell timeline, how much time and money our customers have saved by using Snyk, and what some of those customers have said about their experience.
Auto-Erkennung und -Fixing von Schwachstellen
Snyk bietet Security-Fixes als Pull-Request mit einem Klick und Korrekturempfehlungen für Ihren Code, Abhängigkeiten, Container und Cloud-Infrastrukturen.
