Cloud Security at Blackhat and Defcon 2022
Shilpi Bhattacharjee
6. September 2022
0 Min. LesezeitThere’s a week and bit in Vegas where most of the infosec community, hackers, blue teamers, red teamers, bug bounty hunters, and now cloud security researchers come together to hang out at a cabana, attend some crazy parties, learn, and share all things cybersecurity and hacking. With talks, workshops and training hosted by Blackhat, Defcon, Bsides Vegas,and The Diana Initiative — welcome to Hacker Summer Camp.
What is Hacker Summer Camp?
It is a term that has been given to a week and bit of conferences and events that typically held in the city of Las Vegas. The conferences that form part of Hacker Summer Camp include:
Blackhat -Currently in its 25th year, it was started with the intention of briefing the information security community about what the blackhats were up to. It’s one of the more formal and corporate events at Hacker Summer Camp, and usually has talks (which they call briefings) and workshops/trainings of a more technical nature than its contemporaries. There were heaps of swags giveaway too, which is always fun for those of us who secretly want to increase our workout t-shirt collection (it’s for a friend that’s why i need 2 :D).
Defcon -Now in its 30th year, Defcon is the largest hacker conference. It's popular for its village, which are like mini meetups of their own, and badge cultures where each village has their own badge. There is a village for anything you can think can be hacked, and for various communities. For those interested in Cloud Security, there is the Cloud Village, which certainly has a lot of cloud security talks and activities, but you may also find cloud security talks and panels at Appsec Village, Blue Team Village, and some others. The conference does not have any corporate sponsorship, and is supported solely by the proceeds from selling the badges and T-shirts. Each badge is designed to be hackable, and some have parts that involve talking to other attendees to help hackers connect. You can find the full list of villages here.

Bsides Vegas- very much like other Bsides Events, it’is a community event that runs besides other conferences — in this case Blackhat and Defcon. They feature talks and trainings for a variety of topics in Cybersecurity.
The Diana Initiative is a conference dedicated to making the cybersecurity industry more inclusive.
Who is Hacker Summer Camp for?
BSides Vegas, Diana Initiatives, DefCon are all community events, which means they’re a lot less formal, and have more security games like CTF, Lock picking, and re-con games. These events are really for anyone interested in cybersecurity, looking to connect with others with similar interests and wanting to learn from peers.
Black Hat is a more corporate event for CISOs, cybersecurity leaders, practitioners, and those looking to evaluate products they want to purchase — or in some cases check out the competition and envy their booth design or swag giveaway. BlackHat kicks off with CISO Summit, followed by 2 days of Briefing (aka Talks) and Training (which in some cases starts a few days before). There is also the Arsenal where a lot of people would present their open source tools.
CISO Summit perspective
We spoke to many CISOs about why they attend Blackhat or Defcon. A lot of CISOs prefer going to BlackHat just for the CISO Summit for the opportunity to meet other CISOs from all over the world (visitors from 100+ countries at most Black Hat events), in addition to seeing friends and colleagues that have been attending since they started in cyber security.
Some of the crowd favorites from CISO Summit this year was Cyber War 2022 from Kenneth Geers, and Unifying Asset, Attack Surface, and Vulnerability Management from Daniel Miessler. Overall, all the CISOs we spoke to felt that attending the CISO Summit alone was worth their time, even if they didn’t get to attend any other event.
Are things going to get worse before they get better?

The keynote this year at Blackhat was from Jeff Moss, founder of Blackhat, and Chris Krebbs, the former director of CISA. Blackhat was started 25 years ago to brief those attending on what blackhats were up to, and inform consumers about buying secure products — something we’re still working on as an industry.
The keynote highlighted that today’s cyber security is dealing with the unintended consequences of technology. The landscape is shifting, more things are connected and open to the internet, there is more data, and the industry is growing more complex and mature. Technology vendors are addressing these issues, but is it at the pace we need to keep up?
There was a reminder of something we often acknowledge in cyber security — that security works within a larger ecosystem, and within organizations that focus on productivity, security is seen as friction, as slowing things down. With the acceleration to the cloud and digital transformation in the last few years, we have added flexibility, elasticity, productivity, and efficiency, but reduced transparency and added complexity. There has been an explosion of SAAS building products that are insecure by design due to market pressures.
Chris Krebbs shared a valuable quote from Daniel Miessler “software remains vulnerable because the benefits of insecure products far outweighs the downsides” — once that changes software security will improve.
Top Cloud Security Topics
Supply Chain is where the targets are
Supply Chain Security remains on people’s mind, especially CI/CD pipeline and API security. As Chris Krebbs mentioned, “Why do you rob a bank? That's where the money is.” This is the same reason our adversaries target the software supply chain, because that's where the access, data, and attacks can be scaled.
Attacks are increasing in both severity and sophistication, and it seems that defenders haven’t adapted at the same pace. Adversary groups possess an increased awareness of incident response techniques and cloud security mechanisms, which are being leveraged in attacks.
In addition to this, CI/CD pipeline is becoming part of standard infrastructure, alongside the increased adoption of infrastructure as code. So, this is becoming the attack surface for supply chain attacks. Talks highlighted that while securing the CI/CD pipeline is beneficial, it is also complex and environments are rarely threat modeled. However, recent high profile compromises have resulted in an increased focus on pipeline and infrastructure security.
API Security as part of securing the supply chain remained top of mind. The control planes of APIs are exposed and well documented, allowing attackers to move laterally between networks and AWS accounts by assuming roles, pivoting, escalating privileges, and leveraging AWS Control and Data Planes to achieve their objectives.
You can’t talk about supply chain security without mentioning open source dependencies, third party code, open source libraries, and shared repositories. There was a nod to this, and attention drawn to the fact that while Russian APTs have garnered much attention, Chinese APTs have been the force behind more attacks than people may realize — targeting the technology sector for economic espionage and intellectual property theft.
We are still overtly permissive
Consistent with what we observed at AWS re:inforce last month, focus of IAM (Identity & Access Management) is still paramount. Researchers continue to find that most cloud identities on production cloud accounts are overtly permissive, more so for CSP-managed policies than customer-managed policies.
In the cloud security world, access keys are the new perimeter, and permissions become the limits for this perimeter. IAM with least privilege is what defines security posture. There are many open source tools available to assist with this, and several of these were mentioned and discussed at the Hacker Summer Camp conferences..
To name a few and in no particular order:
Policy Sentry - Kinnaird McQuade
Iamlive - Ian McKay
Cloud Tracker - Scott Piper
Repokid - Netflix
Iamspy - Nick Jones and Mohit Gupta
PMapper - Erik Steringer
Cloudsplaining - Kinnaird McQuade
Some words of wisdom shared were:
Beware of non-human identities.
Some CSP defaults are an attacker’s best friend.
While logging is important, and better than before, it has limits that we must be aware of and should be contextualized. Logging allows for better permission building.
Are CSP defaults leaving us exposed?
While cloud providers often market themselves as the most secure infrastructure for your code, some may argue their defaults are far from secure. With certificates being issuable without proof of domain ownership, insecure SSH by default, default passwords, and more, the move to the cloud is making it easier for you — and malicious actors — to get into your infrastructure.
Automation accounts function within cloud service providers, and their built-in functionality can often be abused by attackers to gain access to credentials, privileged identities, and sensitive information. Often there are built in blind spots in cloud service provider defaults because of the following reasons:
Critical security areas that are hard to get right, or confusingly misrepresented.
Cloud provider design flaws and backdoors that limit the degree of security that can be reached.
Legacy support and dirty fixes that make for great hiding places for attackers.
There seems to be a rise of cloud security research, with talks from cloud security researchers being presented at Blackhat and Defcon — similar to what we saw at aws re:inforce + fwd:cloudsec. It may be an acknowledgement from the wider cloud security community about the need for such research and databases for repositories.
We also saw vulnerable-by-design tooling presented at the hacker summer camp, flagging the industry’s need for hands-on training in cloud security
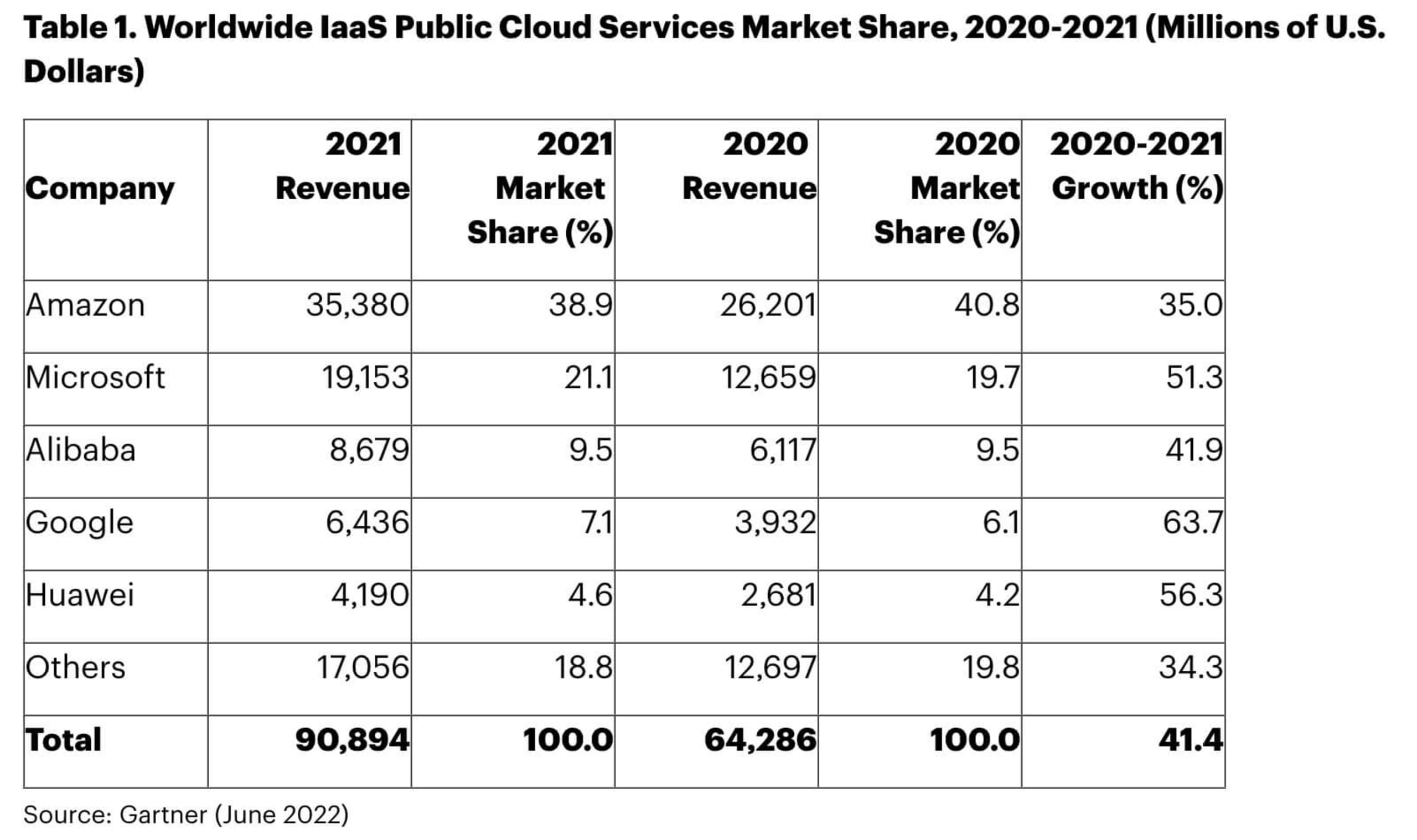
Gartner shared the above chart earlier this year, showing that while Amazon continues to have the biggest market share, there is some shift in the market. There were several azure talks at hacker summer camp, which may either indicate that AWS has previously been covered extensively and therefore there is more interest in Azure talks and gaps in learnings, or there may be an increased adoption of Azure. Some of the interesting insights for AWS came from exploration of the lesser known services, like Amazon AppStream 2.0 — which is a fully managed desktop service that provides users with instant access to their desktop applications from anywhere.
If you follow the buzzword bingo blogs by Kelly Shortridge, there was definitely a solution to most cyber security problems that you can think of. Whether it’s Agentless, CDR (Cloud Detection and Response), EDR for cloud workloads, continuous discoverability, or APIs, there’s a good indicator that Cloud and Data are the two big pillars in this DevOps heavy technology world we’re moving towards.
Hacker Summer Camp wrap-up
Hacker Summer Camp and the conferences that are a part of it offer a truly unique opportunity for cybersecurity professionals, practitioners, and enthusiasts to explore technologies, learn, and unwind with like minded people. Overtly permission IAM, gaps in software supply chain (from CI/CD pipelines to APIs), vulnerabilities identified by cloud security researchers, and gaps in CSP defaults were top of mind, and begged the question — will things get worse before they get better? And as a security community, what can we do to keep pace with this?
As Chris Krebbs aptly put, “the cybersecurity community has a lot of influence, we have to recognise it and own it” and solve these challenges together
Want more? You can check out a list of talks on the Cloud Security Podcast’s page.
Hear the Cloud Security Edition of the Hacker Summer Camp.

