Recap: Stress-Free Security for Devs and Ops on AWS
April 3, 2023
0 mins readSnyk recently hosted a half-day virtual event focused on security for application workloads running on AWS. The event was broken into six sessions spanning topics like developer challenges in cloud-native AppDev, top vulnerabilities from last year, hands-on workshops with industry-leading technology vendors, and several other subjects that help enable engineering and security teams to build a successful DevSecOps workflow.
Below is a recap of the security themes covered during each session.
Opening Keynote: 12 Factors of pain and suffering for developers
Randall Degges, Senior Director of Developer Relationships & Community at Snyk, led the first session of the day. Calling it his personal “therapy session,” Randall gave viewers a hysterical look into the pitfalls he experienced as a business owner and developer building applications on AWS and, most importantly, what he learned from those mistakes.
Randall called his session 12 Factors of Pain and Suffering for Developers, modeled after Adam Wiggins’ 12-factor application: a methodology for building simple, scaleable, and dependable apps in cloud environments. Randall touched on each of the 12 factors by explaining the mistakes he’s made using scenarios from his time as both an individual contributor and a business owner. We’ve recapped one of our favorite anecdotes from his presentation here!
The fourth factor of Wiggins’ 12-factor application implores developers to “treat backing services as attached resources,” or, as young Randall learned the hard way, “build properly from the beginning.”
As a 12-year-old, Randall started a blog he hand-coded and hosted on a shared web host. The blog was doing well until college-aged Randall used his blog space to share pirated movie links (during a time when Netflix content arrived in the mail). Pirating and sharing these movies made him popular on campus — but his web host quickly ran out of space to host the influx of content, forcing him to move his hand-coded PHP application to a proper architecture. This was a long and arduous task, as one might imagine.
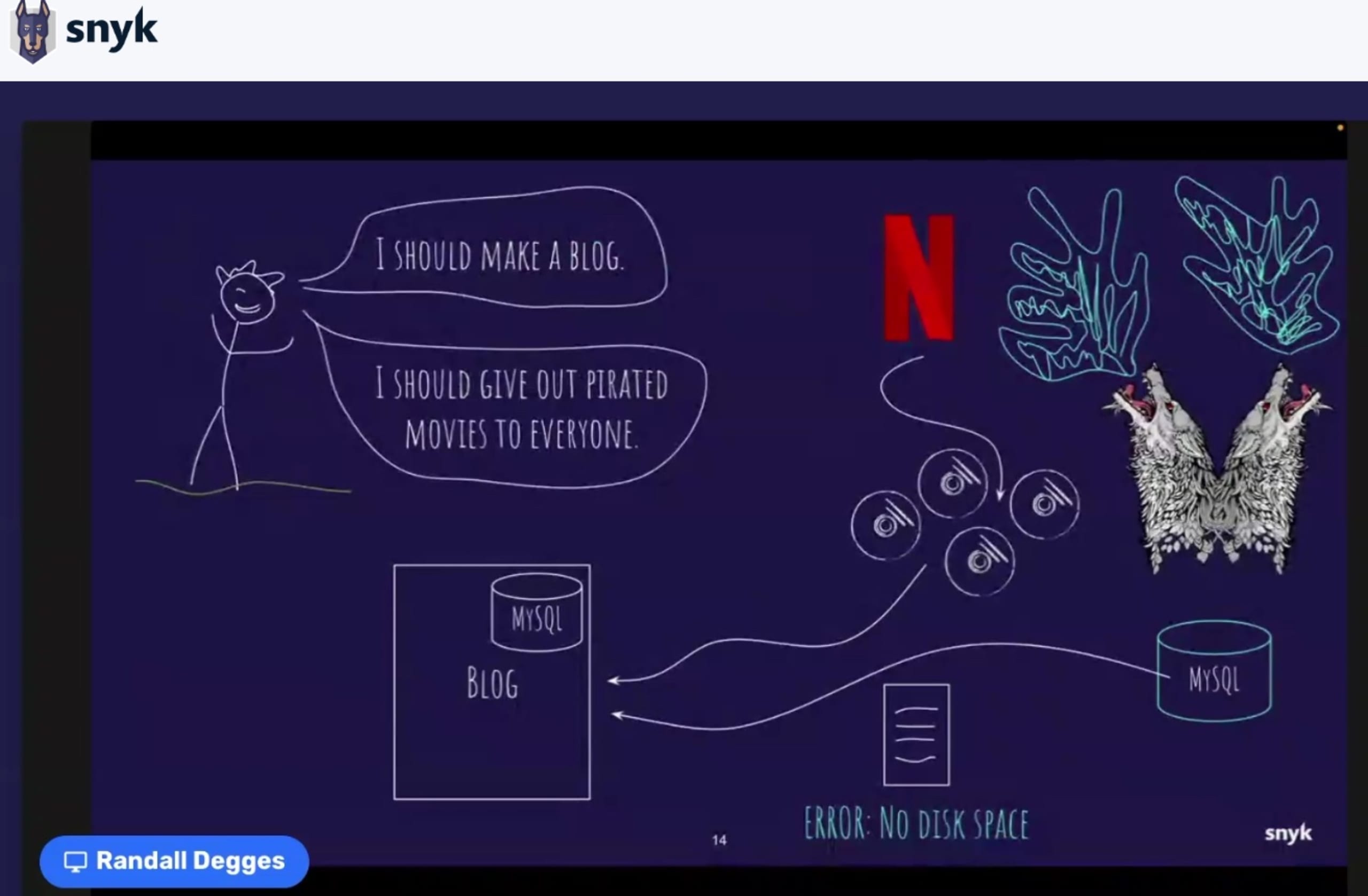
Randall’s session reminds us, in 12 different ways, that even experienced developers make mistakes.
Watch the session here!
Session 2: Snyk's Top 10 vulnerabilities devs should know
Vandana Verma-Sehgal, Senior Developer Advocate at Snyk and OWASP board member, led the second session of the Stress-Free Security Summit, titled Snyk's Top 10 Vulnerabilities Developers Need to Know.
This session is perfect for those familiar with the OWASP Top 10 who are looking to go even further to keep their applications secure.
First, Vandana laid out some hard truths:
Organizations of all sizes rely heavily on software, and much of that software contains OSS components.
There are major risks when using OSS. For instance, defects in small libraries can cause systemic vulnerabilities, similar to Log4J.
Traditional cybersecurity threat models are no longer sufficient for remediating OSS risk.
Then, she shared best practices around how to mitigate some of the most critical vulnerabilities across the software supply chain, guiding viewers on how best to:
Stay ahead of application security risks by addressing these 10 top critical vulnerabilities.
Identify the most recent and impactful open source vulnerabilities so their AppSec teams can defend against them.
Know which threats to prioritize to mitigate risks to applications.
This session is full of valuable insights into the changing landscape of cybersecurity threats. It offers practical guidance to help developers stay ahead of security risks in their application workloads and to mitigate potential vulnerabilities faster and more efficiently.
Hands-on Workshops: Securing Your Code and Cloud Configurations with Atlassian and HashiCorp
The Stress-Free Security Summit included two sessions that allowed attendees to get hands-on experience in securing their application workloads and the configuration of their cloud environments. In one session, attendees used Snyk and Atlassian to automate security controls across the SDLC. In the the other session, they practiced defining and securing Infrastructure as Code using Snyk and Hashicorp.
DevSecOps for Modern Apps using Snyk and Atlassian
Marco Morales, Senior Partner Solutions Architect at Snyk, and Tomas Gonzalez,
Snyk’s Technical GSI Leader, hosted a session giving attendees hands-on experience using Snyk’s unique first-party integration into Atlassian’s Bitbucket Cloud, allowing users to automatically scan code for security vulnerabilities and receive alerts when new vulnerabilities are discovered. This integration helps teams catch security issues early in the development process and fix them before they can be exploited in production.
If you'd like to experience this workshop, sign up for a free Snyk and Atlassian Bitbucket account, then follow along to build security best practices into your native development workflows.
Securing Infrastructure as Code using Snyk and HashiCorp
At the same time, technology experts from Snyk, AWS, and HashiCorp hosted a workshop showing attendees how to properly define and secure their infrastructure as code in development.
Paul Harland, Channel Solutions Engineer at Snyk, and David Schott, Lead Partner Solutions Architect at Snyk, worked with Raj Jeripotula, Senior Partner Solutions Architect at AWS, and Yash Khemani, Solutions Engineer at HashiCorp, to walk attendees through the workshop.
During the session, they demonstrated how the Snyk and Hashicorp integration allows developers to automatically scan their infrastructure code for security vulnerabilities and receive alerts when new vulnerabilities are discovered, streamlining their infrastructure security with automated security scanning and monitoring.
If you’d like to follow along with this workshop yourself, sign up for a free Snyk and Hashicorp Terraform Cloud account to learn how easy it is to scan and deploy an infrastructure-as-code (IaC) project to AWS.
Watch the session here!
Customer Interview: The Value of Developer Security with Acuity Knowledge Partners
During this session, Frank Fischer, Senior Product Marketing Manager at Snyk, interviewed Sameer Goyal, Director of Engineering at Acuity, on The Value of Developer Security. Having been a Snyk customer for several years, Sameer Goyal shared his experience transitioning to a developer-first mindset to properly prioritize application security.
During the discussion, Sameer explained:
Acuity's security challenges in migrating and modernizing application workloads, and how his team integrated Snyk into their development pipeline.
The value they’ve seen from implementing Snyk and how it has helped them catch security issues earlier and faster.
His real-world perspective on cultivating a security culture within development teams and how Snyk helped him achieve that goal.
After implementing Snyk, Acuity was able to stay on top of the security and compliance requirements expected by its financial services customers, improving the security posture of their applications without losing agility or speed in development.
Watch the session here or read Snyk’s customer value study.
Closing Keynote: Cultivating developer security
Developing secure software is crucial in today's digital landscape, and cultivating developer security is an essential part of the process. So it makes sense that the Summit's closing session focused on facilitating a successful DevSecOps workflow using developer-focused security tooling!
Clinton Herget, Field CTO at Snyk, hosted the final session of the day, Cultivating Developer Security. He covered key concepts of a rapidly evolving security landscape, including what's changed for developers, why developer security matters, and best practices around people, process, and tools.
Throughout his session, Clinton noted that security programs have evolved to adapt to Agile development, DevOps pipelines, and faster deployments. The shift towards DevSecOps has resulted in a significant ownership shift of security to development teams. Engineering managers must adopt new security practices to take responsibility for security, including organizational, process, and tooling challenges. Clinton's key to a successful DevSecOps motion: don’t overwhelm your developers!
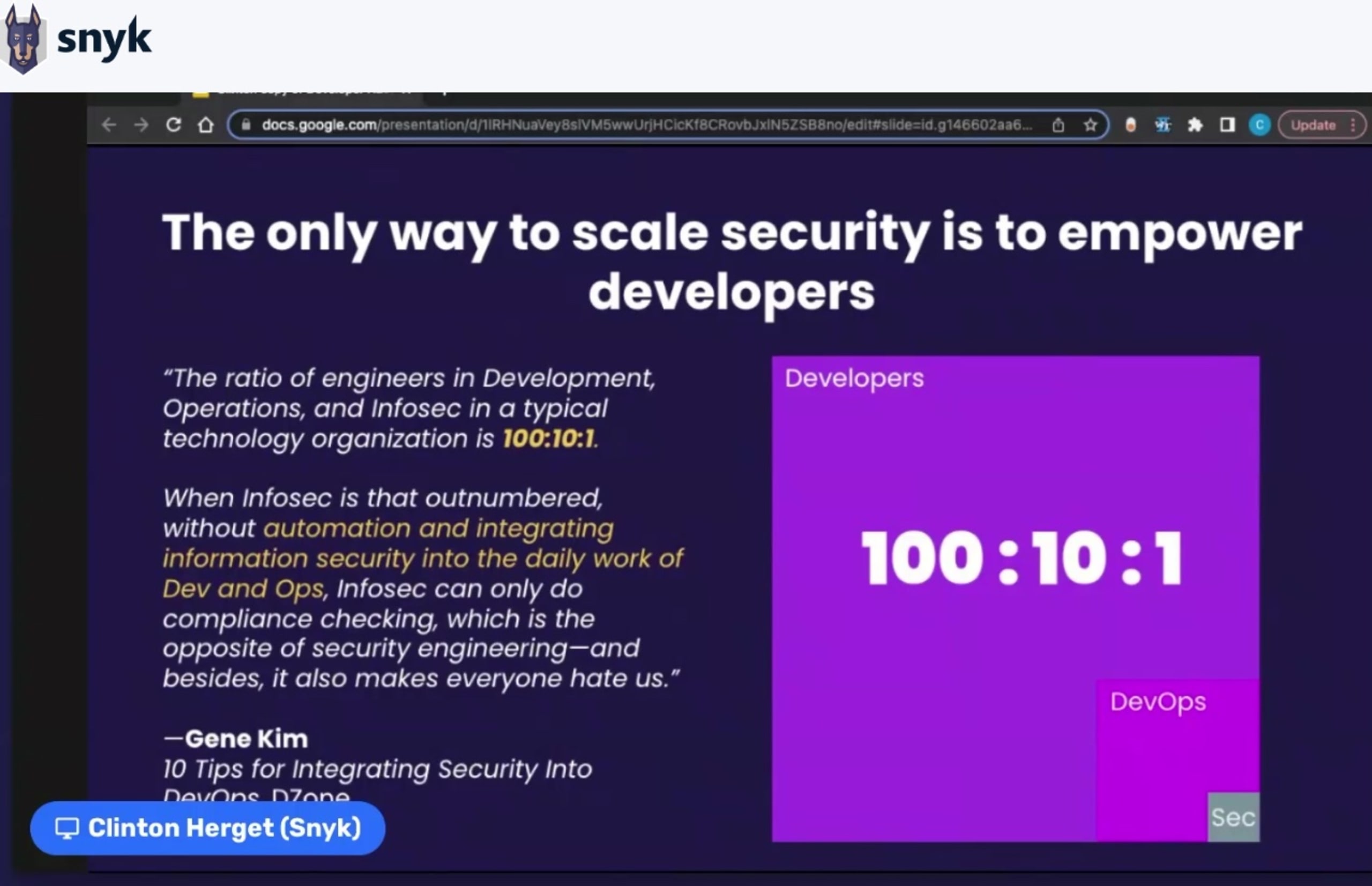
Clinton made an important point in showing how other modern organizations have successfully achieved a developer security culture, and offered tips and best practices for improving developer adoption of the right security tooling based on each company’s security needs. He also highlighted common pitfalls to watch for when trying to fit traditional security processes and tools into modern application development workflows.
ICYMI
You can still catch all the sessions of the Stress Free Security on AWS summit on demand! If you enjoyed this content and would like to learn more about Snyk's developer security platform, book a live demo with a security expert, or try Snyk for free!
