Protect container images directly from your registries
Liron Lifshitz-Yadin
April 30, 2019
0 mins readWe’re happy to share that we are continuing to extend our Container Vulnerability Management offering, now providing integration with your container image registries as well.
Test, monitor and fix vulnerable images
With Snyk’s new container registry integrations, you can scan your container images for vulnerabilities directly from within your registries. You can also monitor the registry images for any newly disclosed vulnerabilities.
Snyk offers remediation advice when vulnerabilities are found. When you include your Dockerfile for testing, Snyk also offers actionable base image remediation advice.
Docker Hub marks the first container registry with which we can integrate; we’ll soon offer additional integrations, including Azure Container Registry (ACR), Amazon Elastic Container Registry (ECR), Google Container Registry (GCR) and Jfrog Artifactory.
Empowering developers
With the addition of registry integrations, we continue to help developers to implement container security seamlessly. Developers can test and easily monitor their registry images for any newly discovered vulnerabilities, and they can choose the way they wish to be alerted accordingly.
Getting started with Docker Hub integration
A new Docker Hub integration option is now available from the snyk.io Integrations page, as in the following image:

Once you set the integration, you can select and import your images as new projects in Snyk.
The following image shows the Docker Hub repository and tag list:
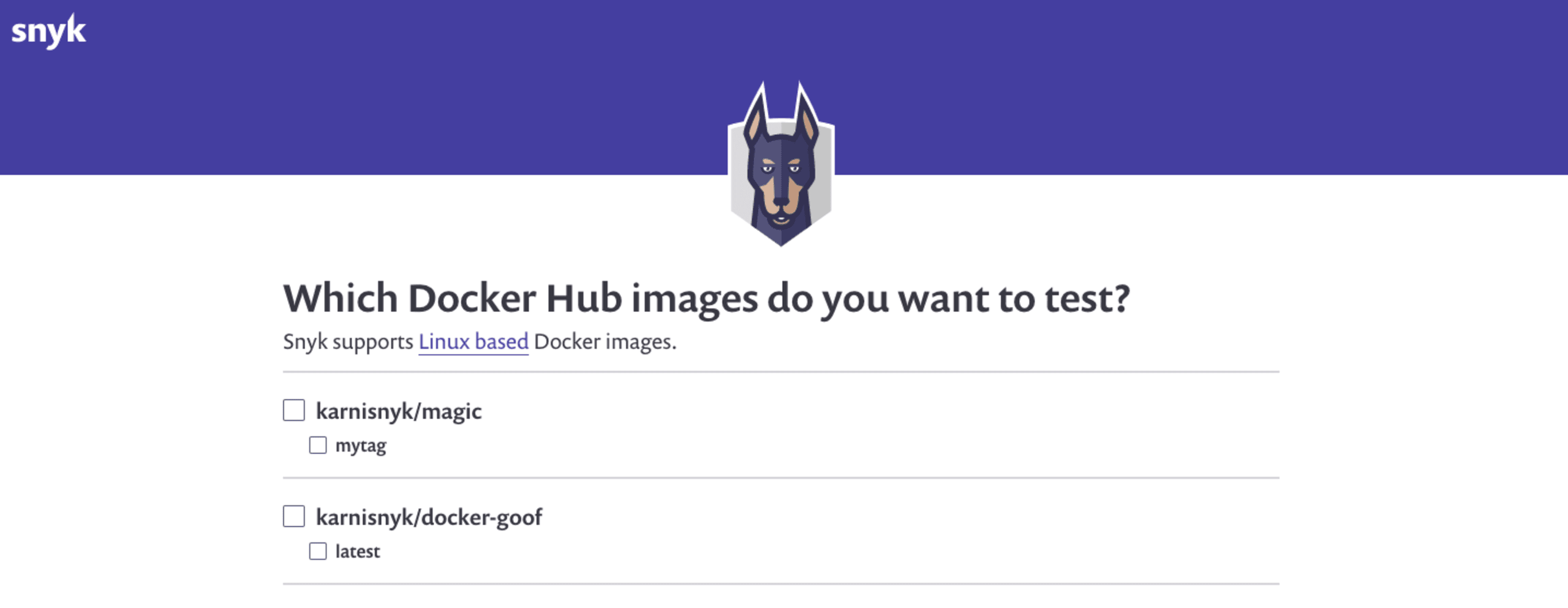
Once imported, projects are grouped according to your Docker Hub repositories, and you can use the new dedicated filter to view only your Docker Hub projects. Snyk monitors these images, testing periodically according to your alert settings.
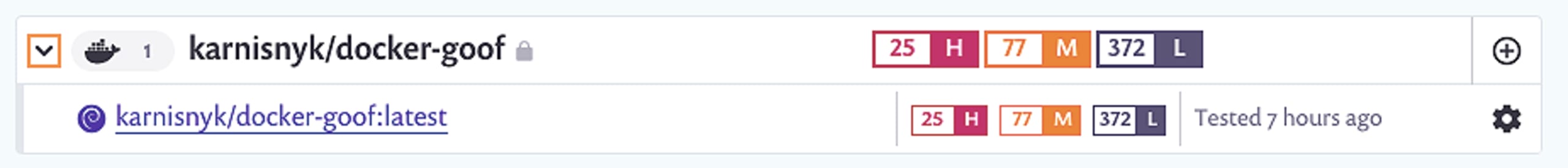
Get optimal base image remediation advice when you add your Dockerfile
For enhanced remediation advice, you can link to the Dockerfile of the image located in the Git repositories. From the Projects list, click the settings cog for the project you’d like to test to link it with the relevant Git repo and Dockerfile, as in the following example:
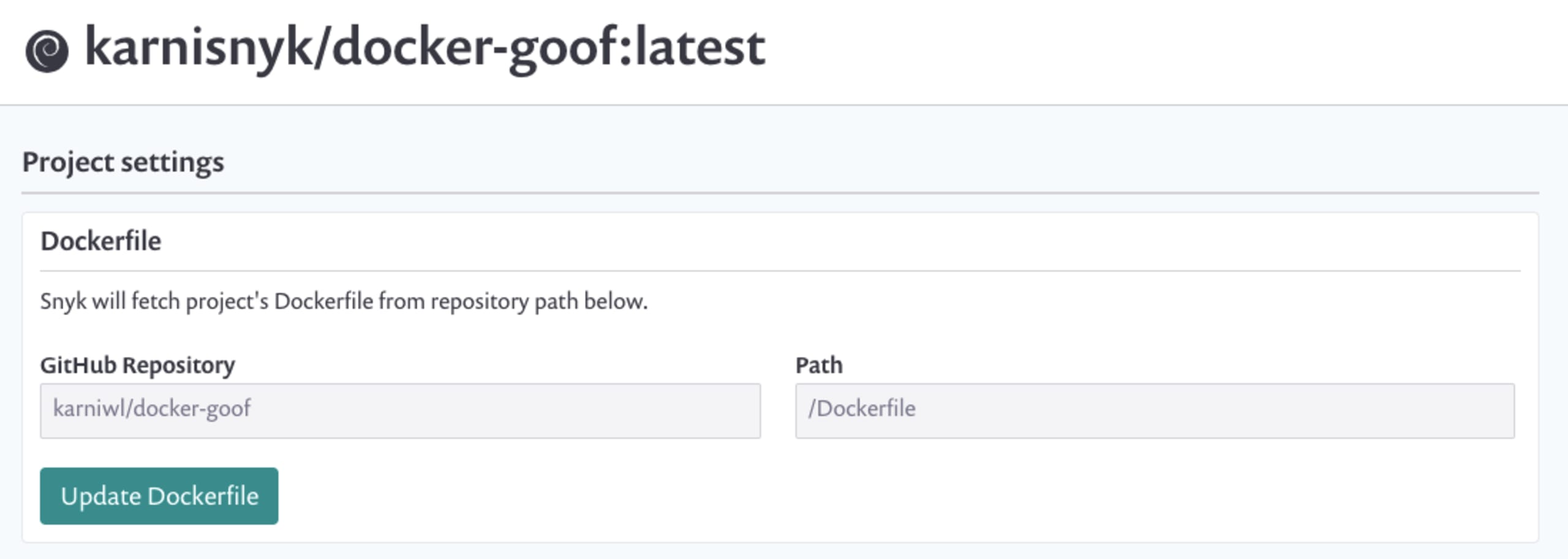
Once added, Snyk offers the remediation advice that is optimal for upgrading your base image to a more secure version; alternatively, Snyk recommends a rebuild when the base image you’re using is outdated.
Once added, Snyk advice can include:
Minor upgrades—the safest and best minor upgrade available
Major upgrades—an option for a major upgrade which will reduce more vulnerabilities but with greater risk
Alternative upgrades—viable alternative image options for replacing your current base image with other, different base images that provide the least amount of vulnerabilities possible.
If your base image is outdated, Snyk also recommends rebuilding your image.
Following is an example of such recommendations:

For more information about our Container Vulnerability Management solution, read our new documentation.
Stay tuned for more announcements coming soon!
Developer-first container security
Snyk finds and automatically fixes vulnerabilities in container images and Kubernetes workloads.
