Automating remediation for vulnerabilities in Python dependencies using Snyk
Daniel Berman
February 26, 2020
0 mins readWe’re pleased to announce improved support for Python in Snyk Open Source, allowing developers to remediate vulnerabilities in dependencies with the help of automated fix pull requests!
The Python Packaging Index (PyPI) had more than 14 billion downloads during 2018, a staggering number by any account (because of a mid-year error in the PyPI statistics service, the actual count is probably much bigger). This number reflects not only the wide adoption of Python as a programming language (#2 language today according to GitHub) but also the challenge of using open source software - a large amount of these packages pull in vulnerable dependencies, both direct and indirect, into projects. Snyk has reported on a few examples in the past year, including a piece on malicious packages.
With this latest enhancement, Snyk Open Source helps Python developers build their apps more securely by not only finding these vulnerable dependencies but also by providing them with automated remediation steps, all within their existing development workflows. To do this, Snyk builds a dependency tree based on the requirements.txt file included in a pip project. These dependencies are then tested against the Snyk vulnerabilities database and any newly found, fixable issue automatically triggers a fix pull request.
Importing your Python projects
Snyk provides a number of integrations for Git-based code repositories, including GitHub, GitHub Enterprise, GitLab, Bitbucket Server and Bitbucket Cloud, which allow you to easily test, monitor and fix security vulnerabilities and license issues in your Python projects and as part of your code management/development workflows.
Let’s see an example of how this works for a sample Python application maintained in GitHub.
In this example, we already signed into Snyk with our GitHub credentials, and so Snyk automatically set up the integration and now displays a list of all the available repositories.
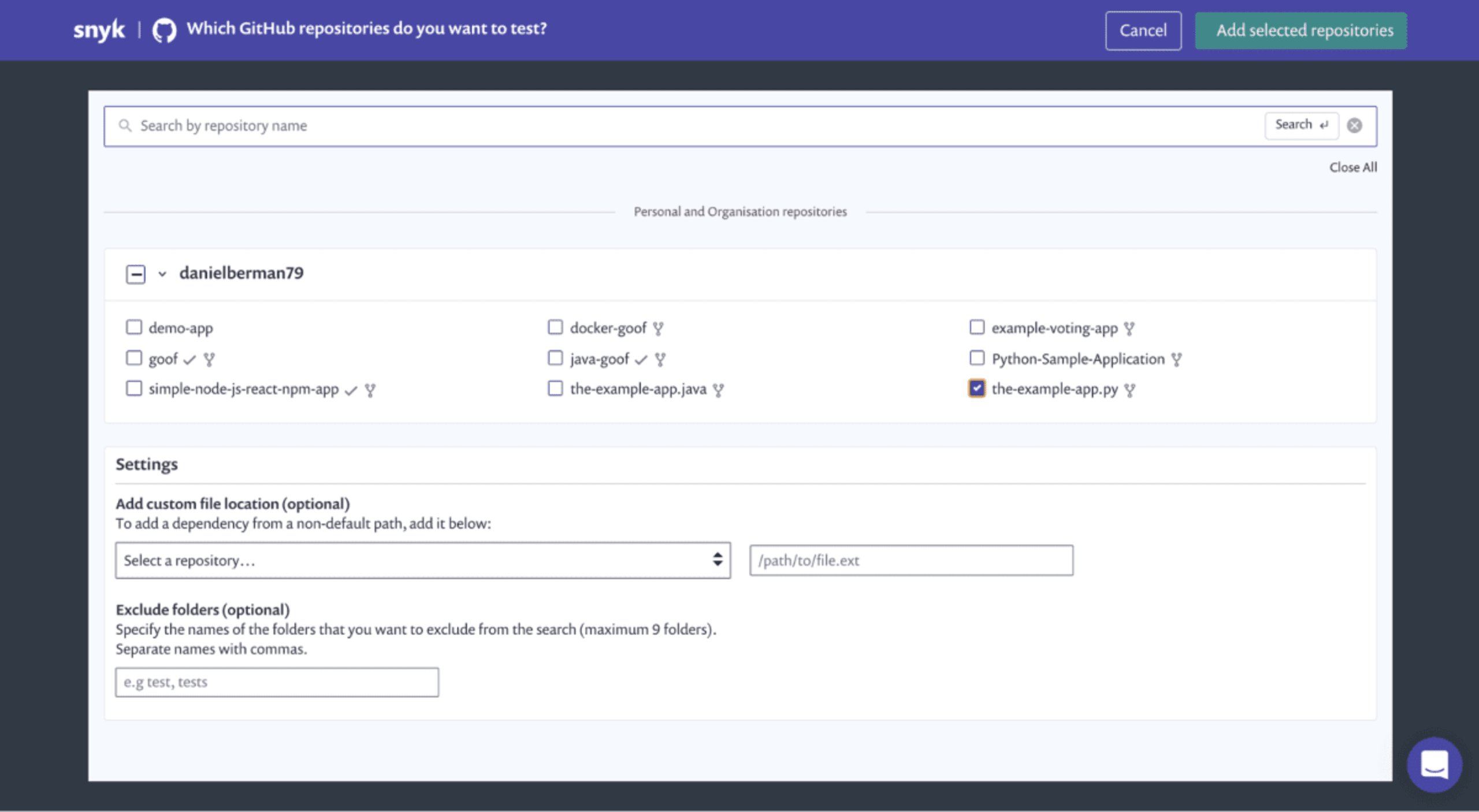
From the Import screen, select the Python project you want Snyk to scan and click Add selected repositories. Snyk scans all of the repositories you’ve selected for their manifest files, importing a snapshot of each file as a separate file.
The Projects page is displayed, and once Snyk finishes importing the Python project, you'll see a success message at the top of the page prompting you to refresh the page. After refreshing, you’ll see your Python project, marked by its Python logo, and listed together with any other project you may have integrated with.
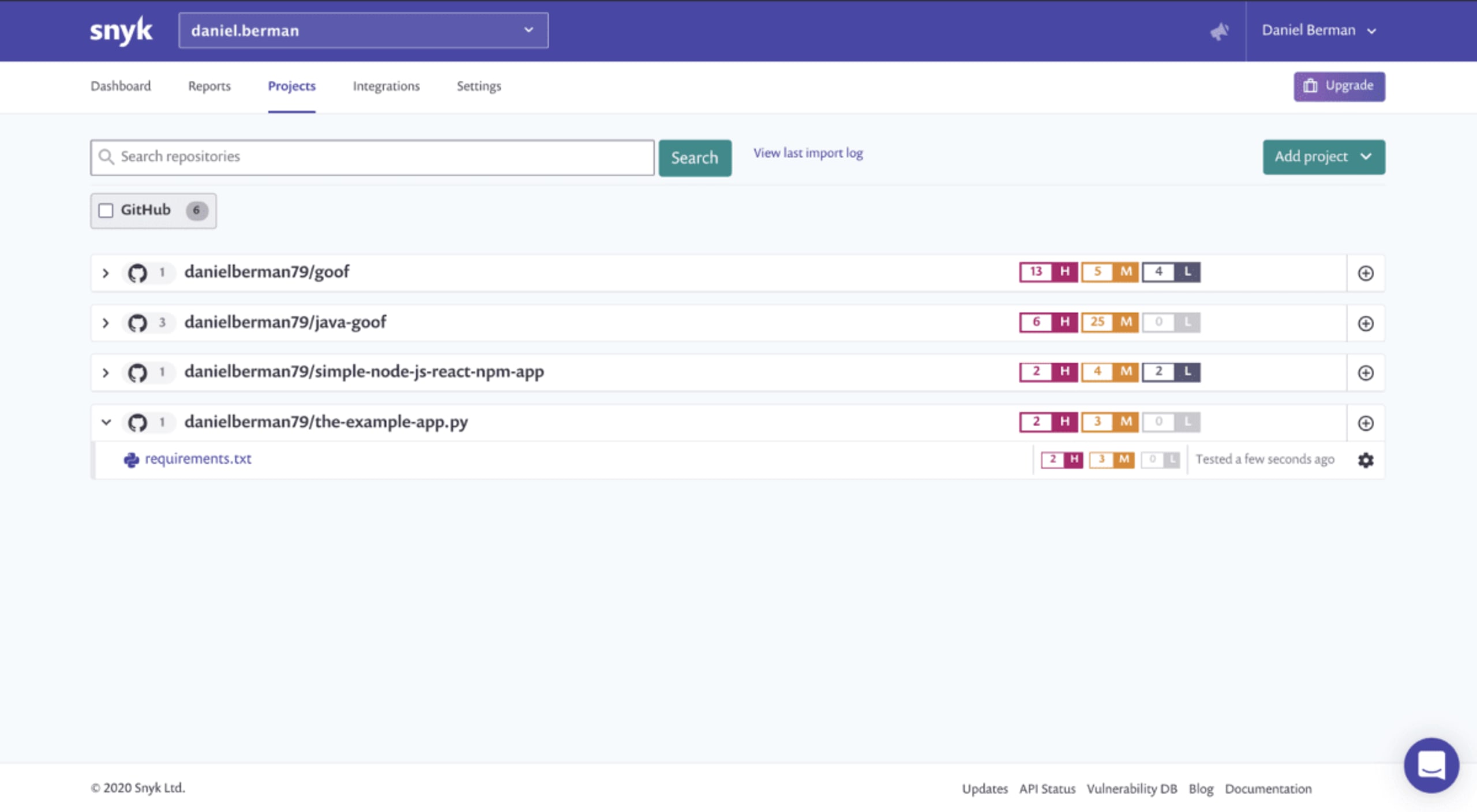
As the numbers indicate for this example, Snyk found a number of vulnerabilities in the imported project. To take a closer look, select the Python app from the Projects list to expand it, and then click the requirements.txt link displayed.
You’re now presented with a full scan report for your project.
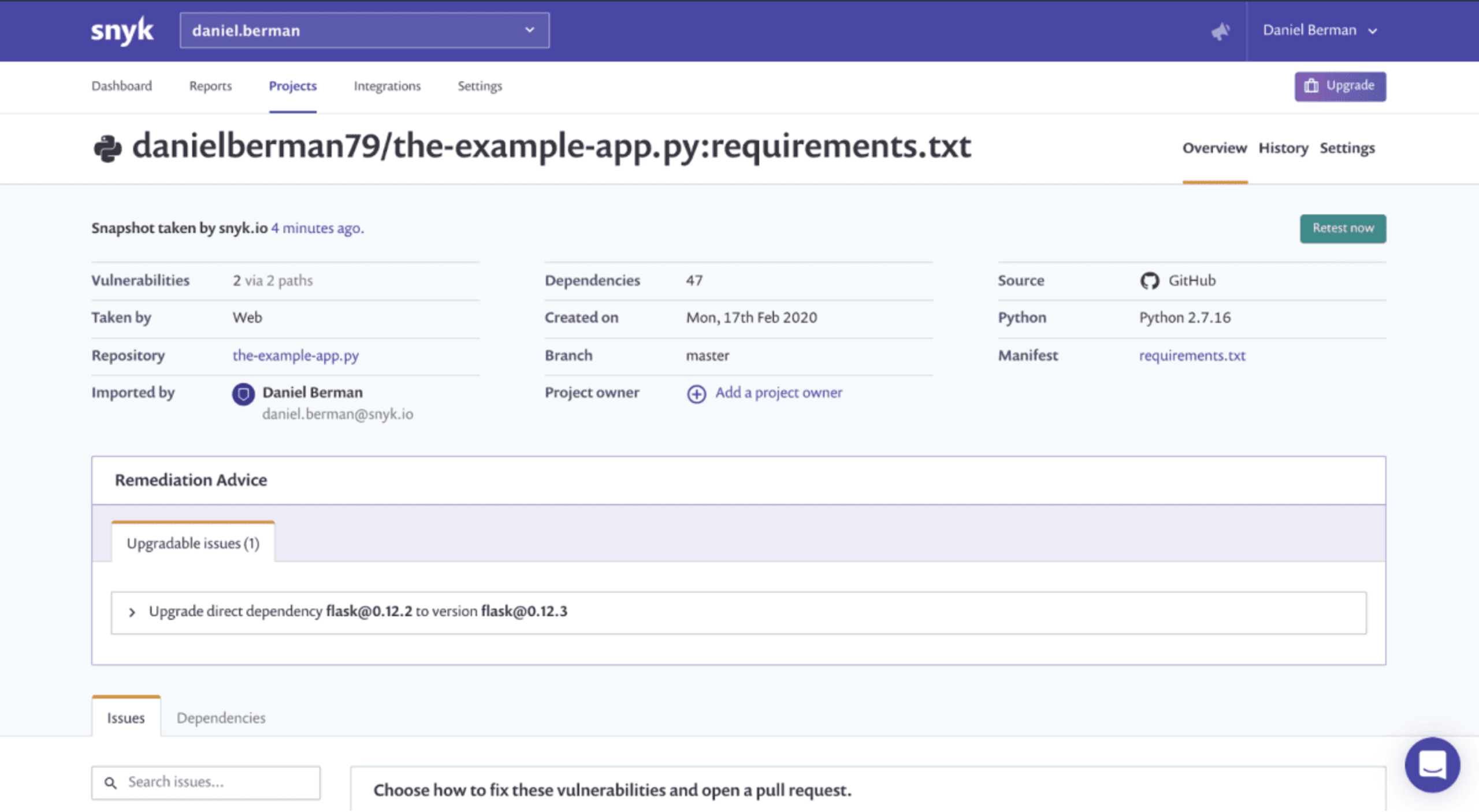
At the top of the page, a bunch of metadata about our project is shown, including the number of vulnerabilities found and the number of paths these vulnerabilities are introduced through.
We are also presented with remediation advice suggesting recommended steps to fix some of the found issues (also a brand new feature, more on this soon!). In this case, upgrading the flask dependency from version 0.12.3 to version 0.12.3 remediates two high severity issues.
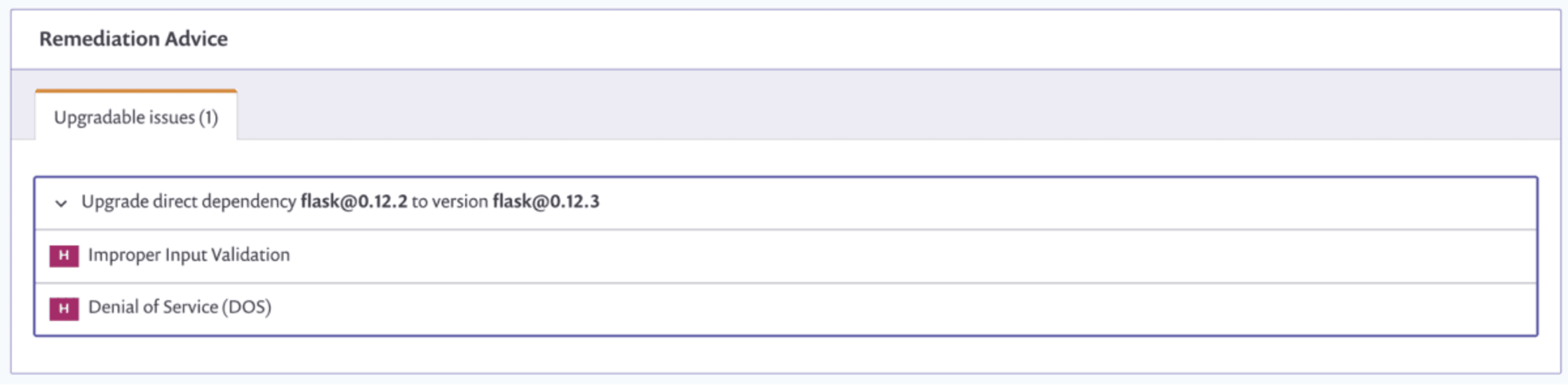
Fix PRs
All the vulnerabilities found in your dependencies are displayed further below, together with contextual information that can help you prioritize the issue and commence remediation if required.
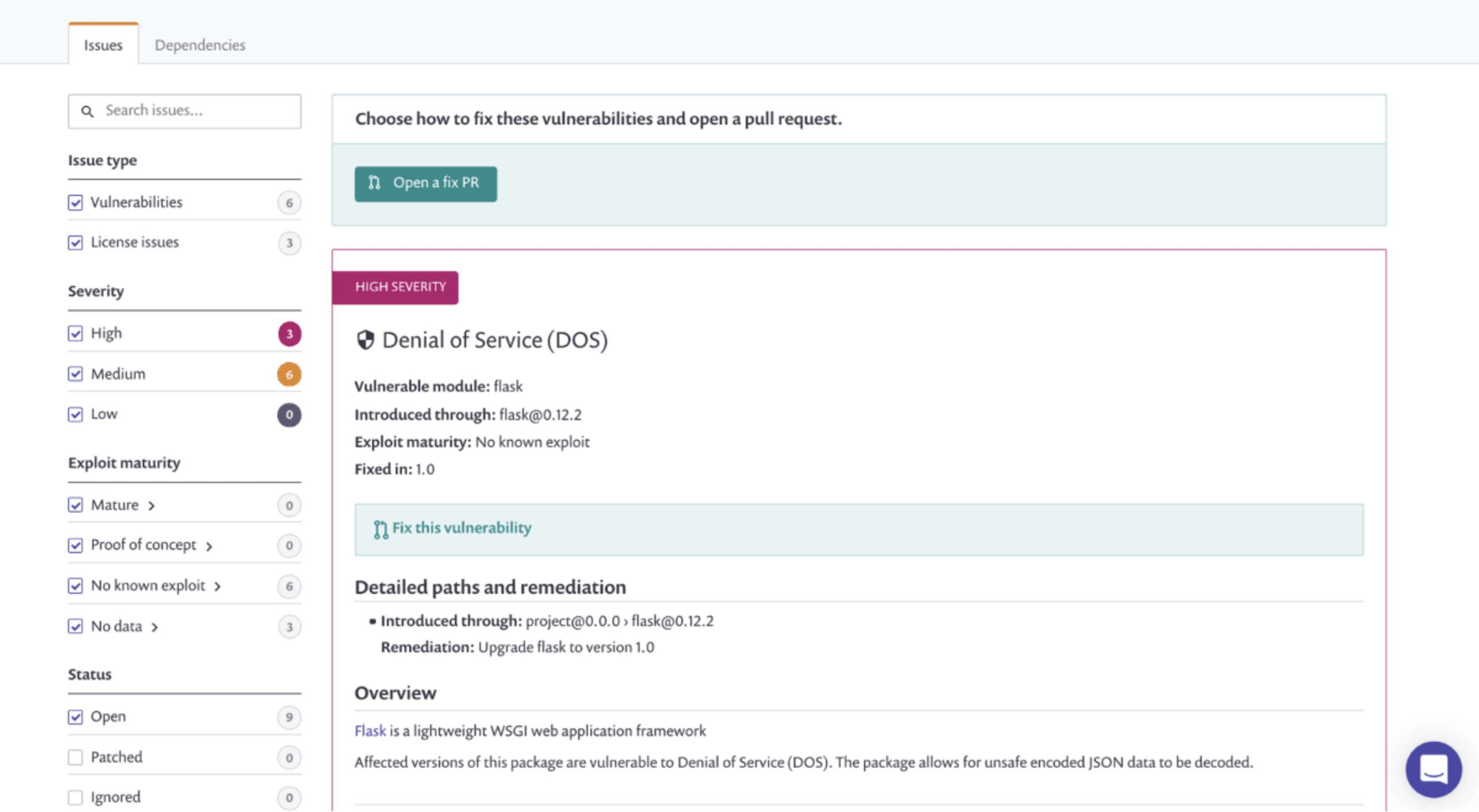
The various filters on the left side of the page help you navigate between the found issues. For example, you can filter by severity to remediate High severity vulnerabilities first or by exploit maturity - an indication of how dangerous a vulnerability actually is (more about exploit maturity here).
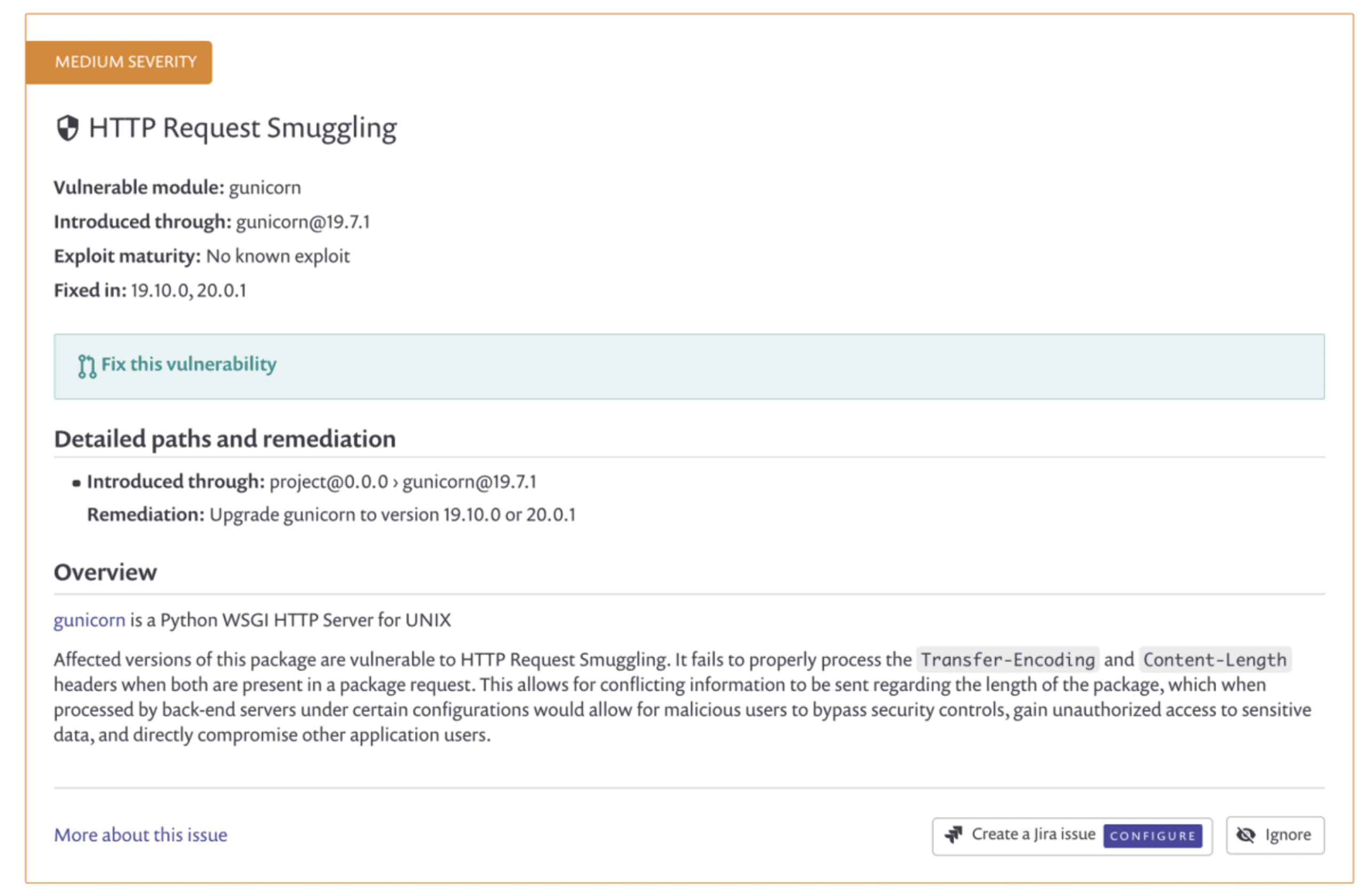
For the vulnerabilities for which Snyk has found a fix, you can create a pull request from within Snyk by simply clicking Fix this vulnerability.
The enhanced support for Python means that pull requests for new vulnerabilities are automatically triggered as well, based on your configurations (more details on this below). Pull requests opened by Snyk display contextual information to help you understand why the pull request was triggered — what changes the fix will apply to your dependencies and more details on the vulnerability the fix is meant to remediate.
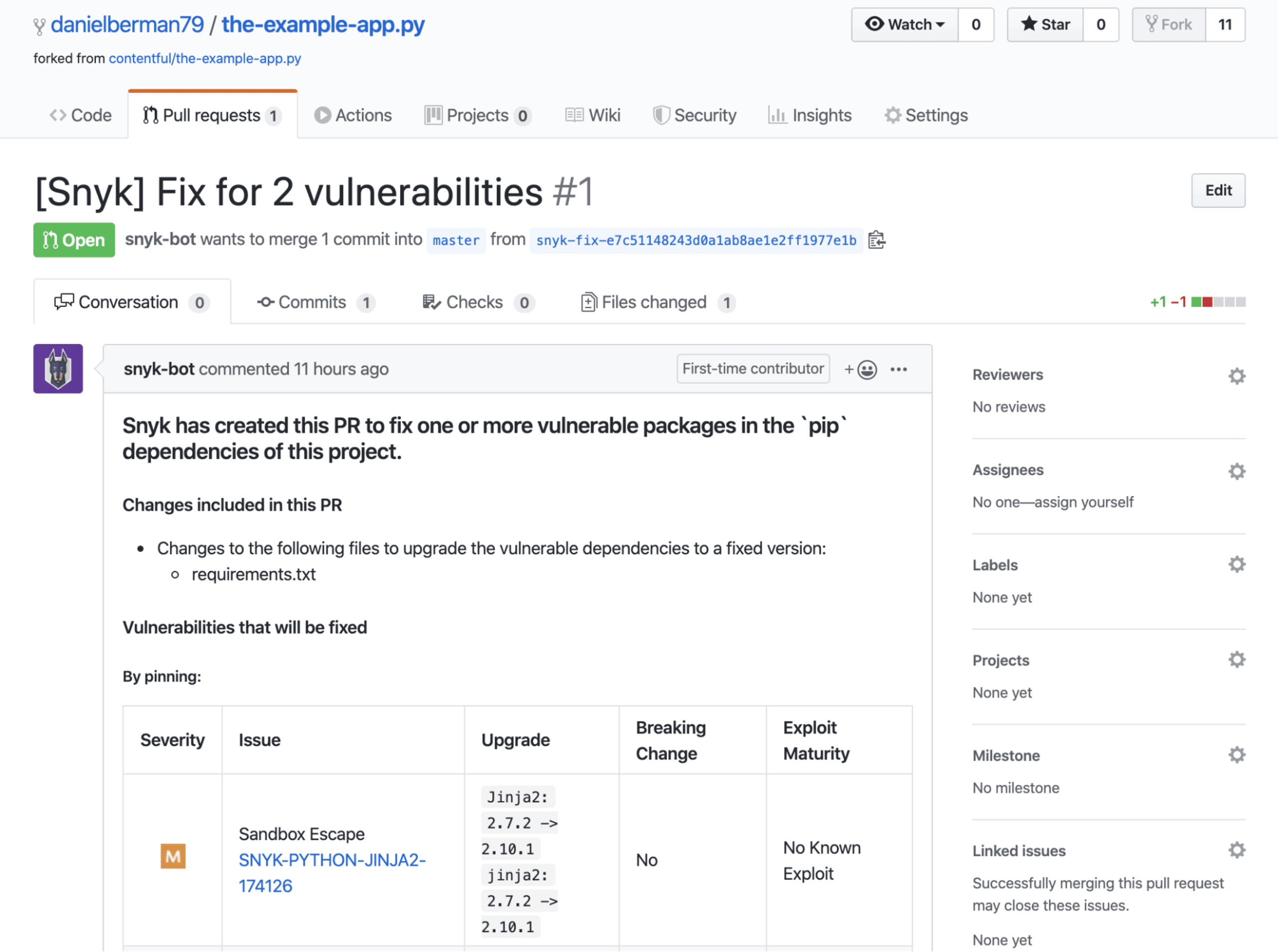
Test PRs
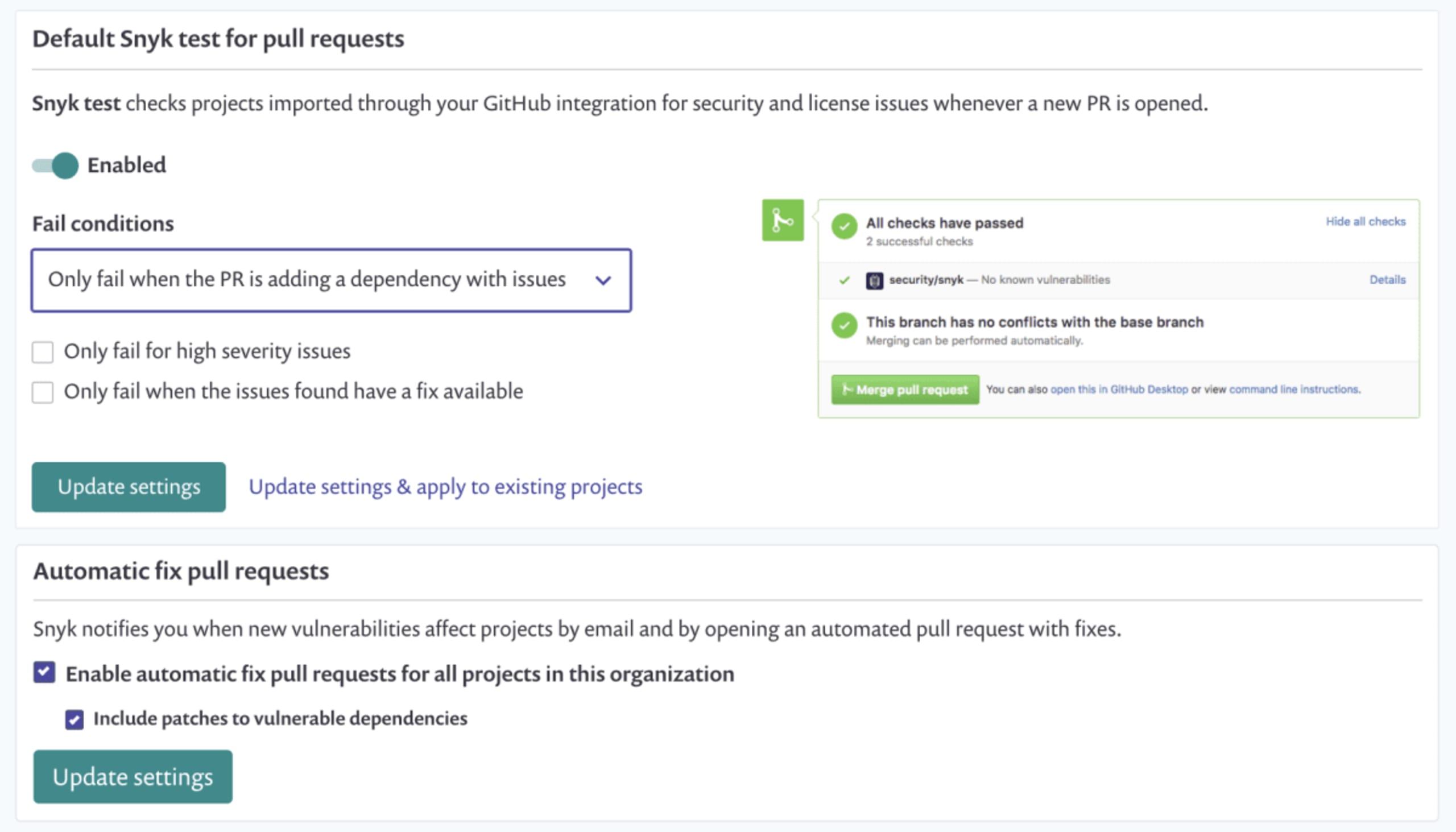
Any new pull request for changes made to the requirements.txt file is automatically tested to make sure you’re not introducing new security vulnerabilities into your project. If vulnerabilities are found, the pull request fails the security test and you can decide whether to continue merging the pull request or not.
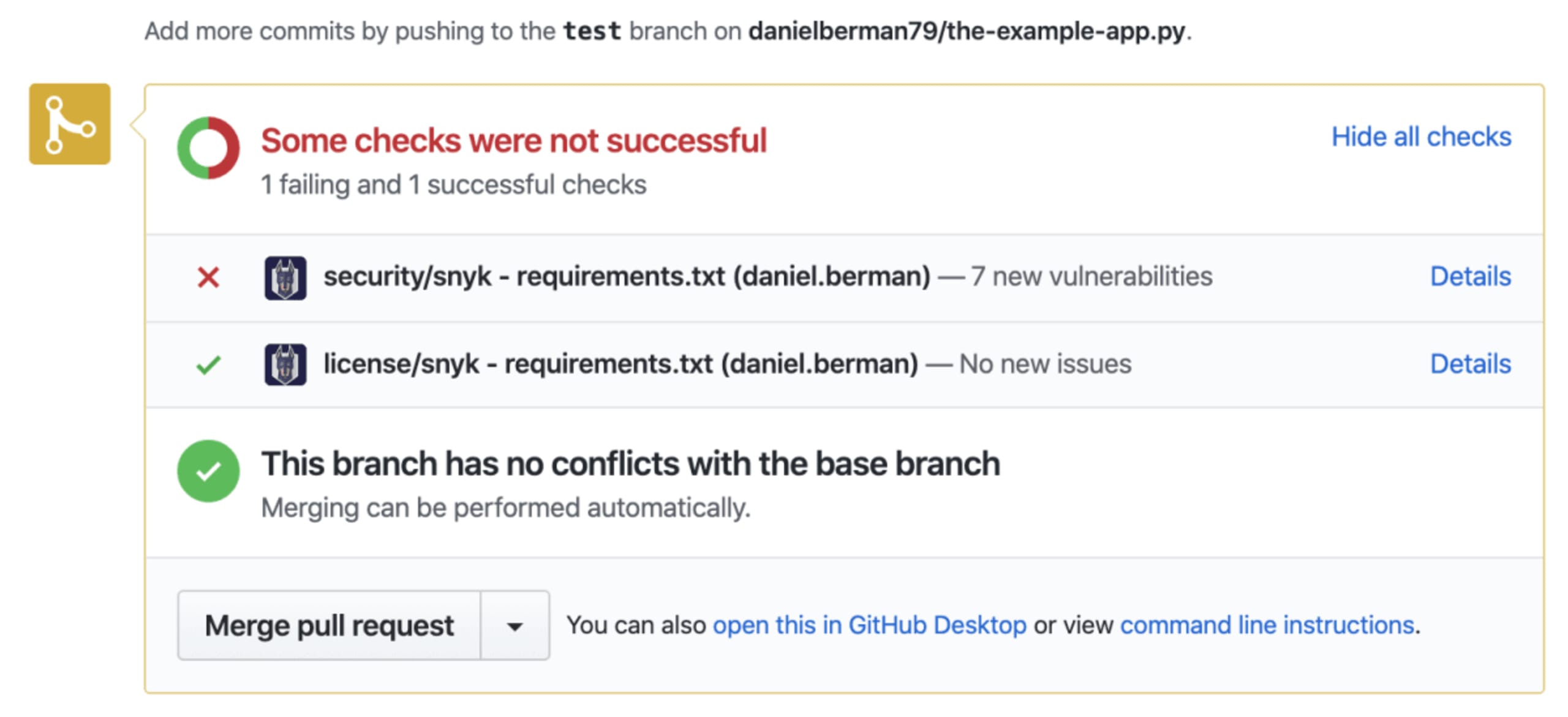
All this automation goodness can be configured. Both test and fix PRs can be disabled. For test PRs, you also have control over fail conditions.
Dev-first security with Snyk
Staying on top of vulnerable dependencies can easily be listed as a top Python security best practice. Easier said than done, right? The ease in which third-party code can be pulled into projects and the overall rise in open source adoption means that the challenge of gaining visibility and control of this code is only getting more complicated.
Snyk was designed to help developers overcome this challenge by providing a developer-friendly tool that integrates natively into existing workflows and helps automate the process of finding and fixing vulnerabilities in open source dependencies.
Automated remediation for Python is provided in all Snyk Open Source plans, including our Free plan which includes unlimited scans for open source projects. To try it out, sign up for an account (using the link below) and start testing. In the meantime, these resources will help you get started with securing your Python projects:
Safe coding!
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.
