4 benefits of visualizing your cloud infrastructure
June 11, 2019
0 mins readEditor's note
This blog originally appeared on fugue.co. Fugue joined Snyk in 2022 and is a key component of Snyk IaC.
As organizations increase their cloud footprint, gaining visibility into their cloud resources becomes an arduous but essential task. It is critical to understand how your cloud resources are provisioned and configured as well as identifying any misconfigurations. Many security and compliance teams address these needs by working with system architects to manually create architecture diagrams for reporting based on cloud console configuration settings, log records, and AWS Config data. This process is tedious and time consuming and not scalable for enterprises with large cloud workloads.
At Fugue, we believe the process of visualizing your cloud resources does not need to be complex and laborious. We are excited to announce the release of the Fugue cloud resource visualization feature which enables DevOps teams, security engineers, and compliance analysts to auto-generate visual diagrams of the resources in their cloud environments. Being able to work visually can improve communication and workflows between cloud teams.
Here are some of the benefits you’ll gain:
Understanding your cloud resources and their relationships
How do you know if your cloud resources are compliant or non-compliant if you don’t know what resources you have? It’s impossible to identify misconfigurations or drift if you can't see the full picture. Fugue enables various teams to visualize their cloud environments to map the current cloud resources, zoom into details on configurations, and identify resource relationships. Interactive diagrams provide visibility into an ever-changing cloud environment and can be automatically generated for new and existing cloud environments.
Demonstrating compliance
As organizations move sensitive data into the cloud, they will be responsible for protecting that data and demonstrating compliance. Compliance teams can quickly audit their cloud environments for potential violations and generate architecture diagrams to prove compliance with PCI, HIPAA, SOC 2, GDPR, ISO 27001 and other compliance standards.
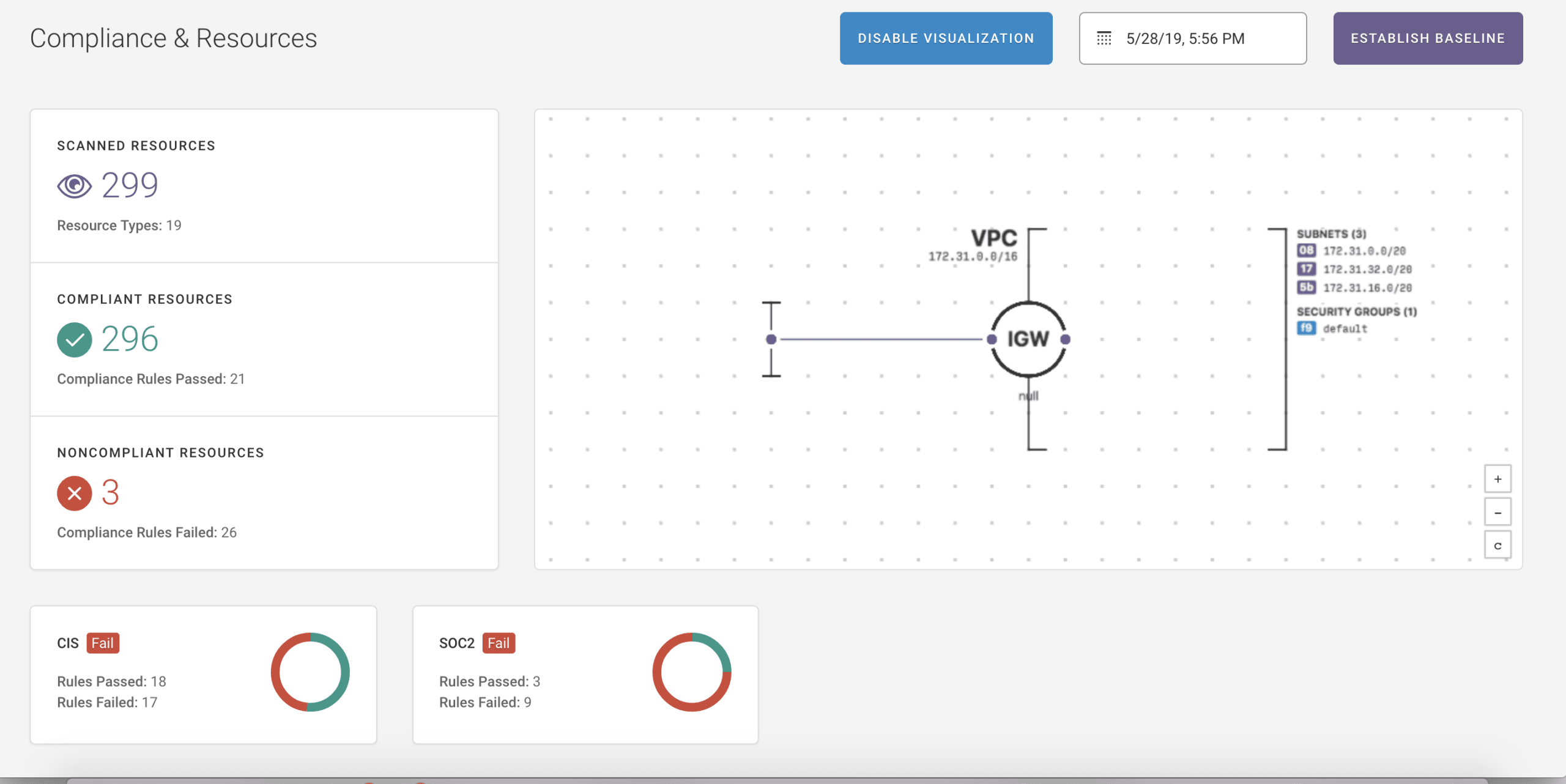
Fugue makes it easy to share your cloud infrastructure diagrams. The auto-generated diagrams can be emailed to executives or auditors to be included as part of other documentation that demonstrate compliance.
Identifying misconfigurations or compliance violations
Fugue identifies compliance violations in your cloud infrastructure, and viewing them in the context of Fugue's dynamic visual diagrams can help teams better understand these violations and prioritize remediation.
With cloud resource visualization, organizations can inspect resource configurations and relationships to view cloud resources that contain compliance violations and security-related configurations.
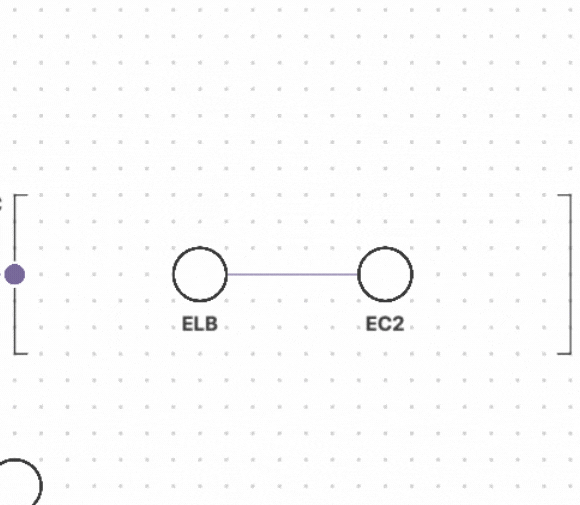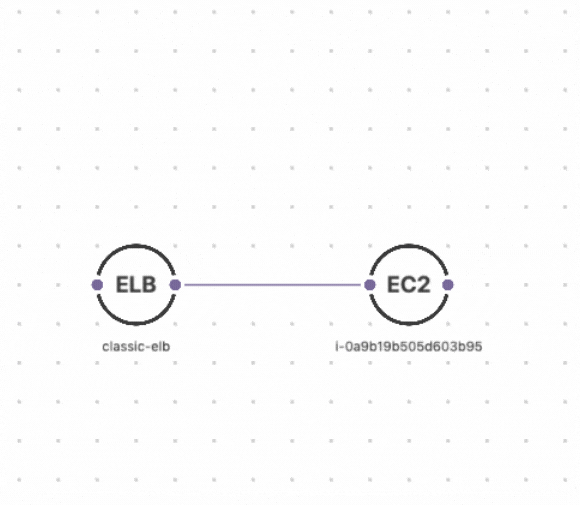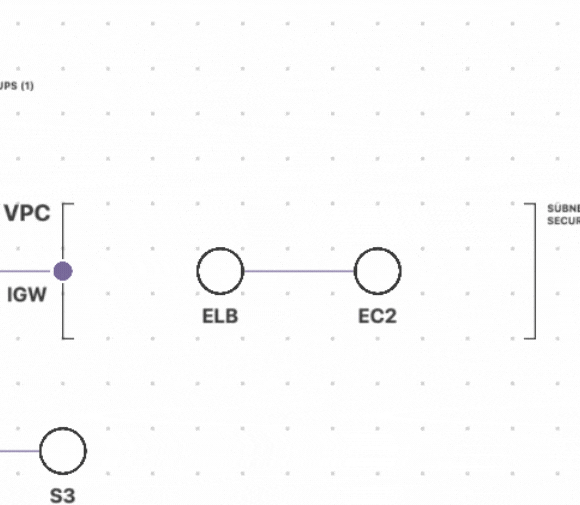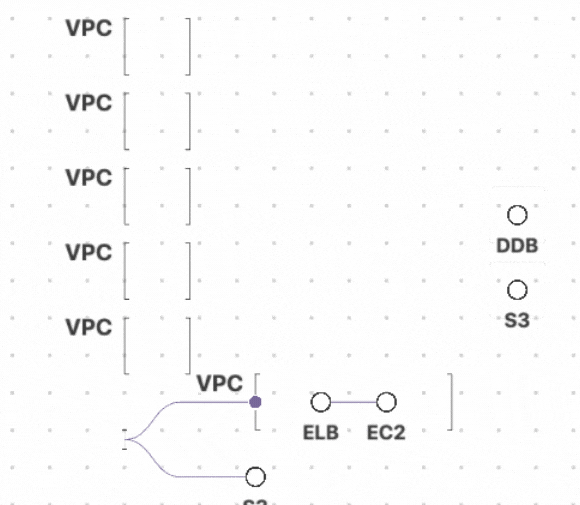
You can generate a cloud resource visualization for any size environment. Cloud resource visualizations display a collapsed view of the unconnected resources, such as AWS S3 buckets, which maximizes space when visualizing large environments.
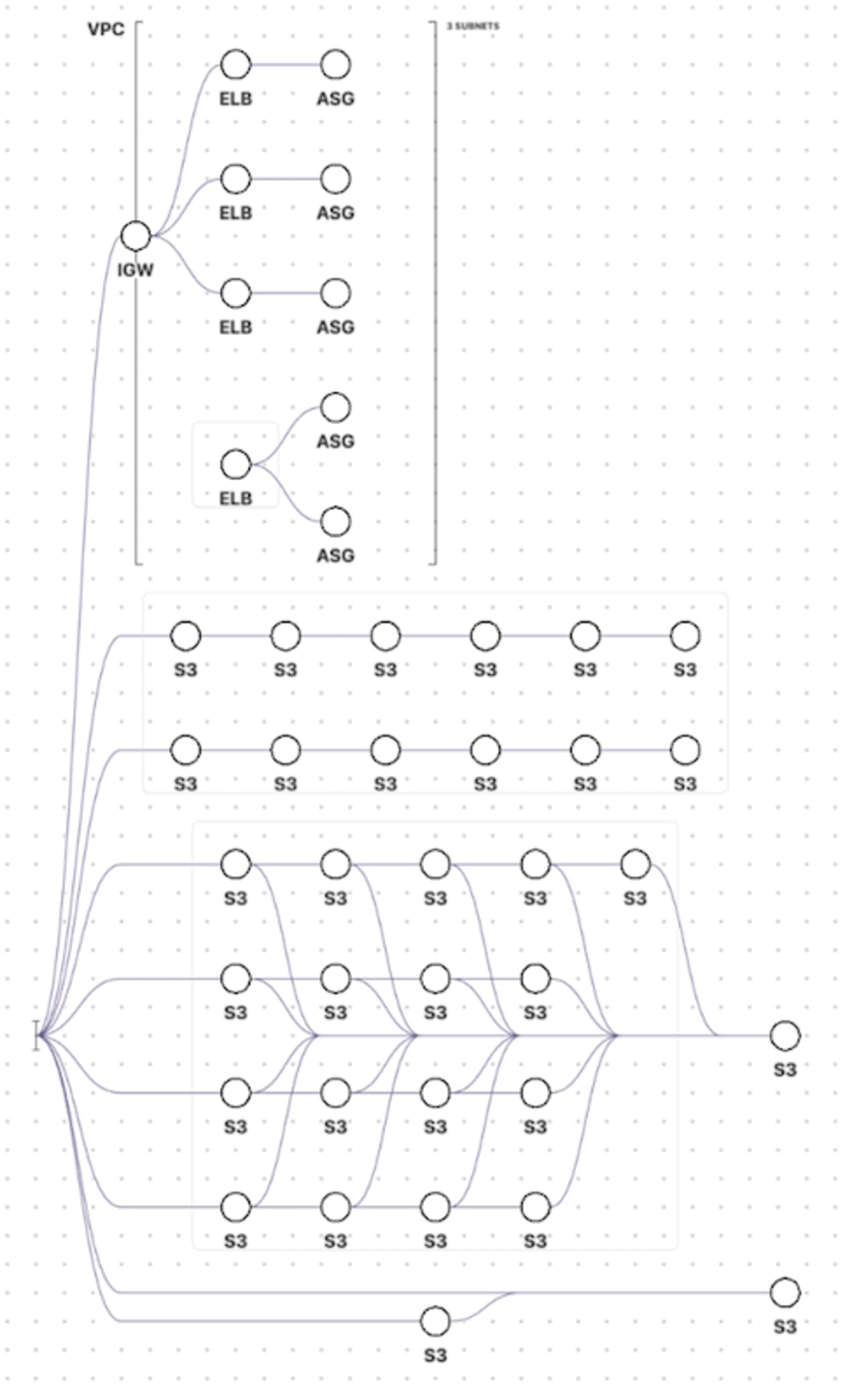
For example, an environment may have 10 unconnected AWS S3 buckets. Fugue users see a collapsed view of the 10 AWS S3 buckets where they are grouped together as 1 consolidated AWS S3 bucket. Clicking the 1 grouped AWS S3 bucket expands the user's view to display the 10 AWS S3 buckets ungrouped.
Understanding infrastructure change
When it comes to cloud infrastructure environments, change is the only constant. In the age of continuous integration and deployment (CI/CD), cloud teams are updating their applications and making changes to cloud infrastructure environments on a daily, or hourly, basis. This is great for innovation and competitiveness, but makes understanding and validating change a challenge.
Fugue’s resource visualization tools helps cloud stakeholders make sense of what can otherwise seem chaotic. DevOps teams can use thee tools to validate that the change they intended to make occurred as desired. And Security and Compliance teams can see when change occurs and quickly understand if these changes have created infrastructure vulnerabilities or compliance violations.
IaC security designed for devs
Snyk secures your infrastructure as code from SDLC to runtime in the cloud with a unified policy as code engine so every team can develop, deploy, and operate safely.
