In this section
Vulnerability scanner: what is it and how does it work?
What is a vulnerability scanner?
A vulnerability scanner is an automated vulnerability testing tool that monitors for misconfigurations or coding flaws that pose cybersecurity threats. Vulnerability scanners either rely on a database of known vulnerabilities or probe for common flaw types to discover unknown vulnerabilities. The scanner logs detect vulnerabilities and sometimes assign a risk score.
What does a vulnerability scanner do?
A vulnerability scanner plays a critical role in maintaining the security of your digital systems. Scanning networks, applications, and devices helps uncover weaknesses attackers could exploit, such as unpatched software, outdated systems, or configuration errors. These tools are invaluable for staying ahead of emerging threats.
Once a scan is complete, the scanner provides detailed reports that outline the vulnerabilities found and offer guidance on how to address them. This allows for prioritization and remediation based on their potential impact, reducing security risk.
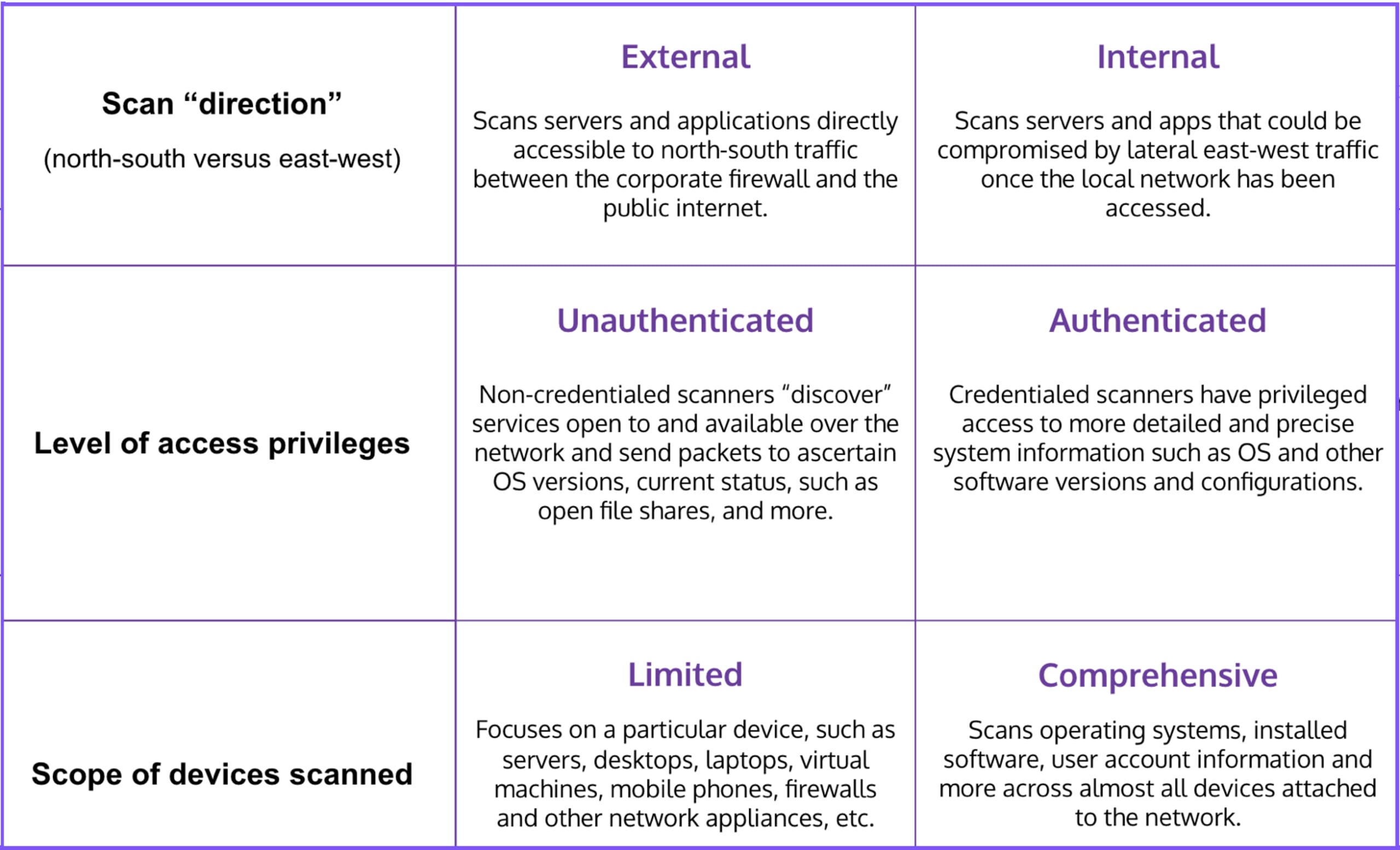
What are the types of vulnerability scans?
Vulnerability scans differ depending on how they are deployed and what they are scanning. Scans can be internal or external, credentialed or non-credentialed, and comprehensive or device-specific. The optimal operating modality depends on what is being scanned: networks, web applications throughout the secure software development life cycle, or open-source codes and libraries.

What Are Vulnerabilities in Cybersecurity?
Vulnerabilities are software coding flaws or system misconfigurations through which attackers can directly gain unauthorized and privileged access to a system or network. Vulnerabilities may pose different levels of risk. Vulnerabilities with known exploits in the wild are considered of high risk and should be prioritized for remediation.
Vulnerability scanners are the front line of vulnerability management. They are essential for identifying vulnerabilities that bad actors could use to compromise systems and data.
3 common types of vulnerability scanners
Network vulnerability scanners
Web application vulnerability scanners
Open-source vulnerability scanners
1. Network Vulnerability Scanners
Network vulnerability scanners monitor web servers, their operating systems, their daemons, and any other services open to the Internet, such as database services.
Network vulnerability scanners work against a database of known vulnerabilities. Many of these databases rely on the Common Vulnerabilities and Exposures (CVE) Program’s free and comprehensive catalog of known software and firmware vulnerabilities. Each standardized record comprises a unique CVE identifier, a brief description, and at least one public reference.
Going one step further, the Common Vulnerability Scoring System (CVSS) enriches the CVE List with a numerical score of the vulnerability’s technical severity. However, proprietary vulnerability databases that continuously aggregate and analyze information from various sources achieve the best network vulnerability scanning results. A good example is the Snyk Vulnerability Database, which is tightly integrated with vulnerability databases, threat intelligence systems, community sources, and academia. Hand-curated by a dedicated security team, Snyk’s Vulnerability Database optimizes network vulnerability scanners so that they can deliver accurate and actionable insights.
This heightened ability to extract maximal insights into network vulnerabilities is also important for operational reasons. The not-for-profit Center for Internet Security (CIS) maintains a set of CIS Controls to help organizations implement cybersecurity best practices. One of the basic controls is that vulnerability management—including scanning—be continuous. However, because network vulnerability scans can cause congestion, scans are typically carried out only once a week. Therefore, these scans must be carried out against an enriched database that provides comprehensive coverage of known and unknown vulnerabilities.
2. Web Application/Website Vulnerability Scanners
Web vulnerability scanners scan application/website code to find vulnerabilities compromising the application/website or its back-end services. They are an essential component of application security testing.
These scanners work against a known list of common exploits maintained by OWASP and others. These exploits use injection and evasion techniques to “hijack” web applications and websites to exfiltrate data, trick users or systems into providing sensitive information, or disrupt application performance. Some of the better-known exploits are SQL injection, cross-site scripting (XSS), man-in-the-middle (MITM) attacks, and malicious code.
Regarding web applications, the only effective vulnerability management strategy is to adopt a shift-left DevSecOps approach and deploy scanners throughout a secure SDLC (software development life cycle). This battery of scanners includes static application security tools (SAST) that automatically scan uncompiled code for vulnerabilities and dynamic application security tools (DAST) that automatically scan compiled code across all environments from testing to production.
Another important tool is penetration testing, which simulates hackers to discover if a web application or website is vulnerable to malicious exploits. There are even website vulnerability scanner online services that conduct third-party penetration testing.
The Snyk SAST solution has been designed from the ground up to overcome the challenges that developers and ethical hackers face with legacy SAST tools, such as taking hours or even days to complete a scan, high false positive rates, and requiring deep security knowledge to remedy issues. With Snyk Code, SAST becomes a seamless part of the development process, providing developers and security teams with real-time and accurate visibility into code vulnerabilities and how to fix them.
3. Open-Source Vulnerability Scanners
Open-source vulnerability scanners are software composition analysis (SCA) tools that scan applications to discover all open-source frameworks and libraries—including all direct and indirect dependencies—and identify vulnerabilities. Some open-source vulnerability scanners also help developers in the non-trivial task of precisely locating the vulnerable code in the codebase.
Seeing that using components with known vulnerabilities is one of the OWASP Top 10 vulnerabilities, organizations must ensure that they are using a state-of-the-art open-source vulnerability scanner. The advantages of the Snyk open-source vulnerability scanner include:
Early detection of open-source code vulnerabilities before web applications or websites have been compromised.
Prompt discovery of all instances affected by a detected open-source code vulnerability so that attackers can be locked out and issues can be remediated faster.
Clear documentation of all open-source frameworks and libraries used in applications.
Ensures compliance with open-source license requirements.
How to Evaluate a Vulnerability Scanner
The good news is that many commercial and free vulnerability scanners are available on the market today. However, the flip side is that many options can make it difficult to evaluate which scanner stack is optimal for your requirements.
The first step is to learn more about vulnerability scanners. OWASP maintains a comprehensive listing of commercial and free scanners, although it does not rank them.
Once you have created a short list of vulnerability scanners, you can try them out. Even commercial vulnerability scanners offer free trials so that you can kick the tires before making a final decision. Given the diverse set of vulnerability scanners that you will have to deploy to achieve end-to-end coverage across all your environments, you may also want to consider a vulnerability management platform that knows how to integrate with all your scanners and correlate their outputs into a single source of vulnerability management truth.
Why is vulnerability scanning important?
Vulnerability scanning is the essential front end of any vulnerability management program. Today, vulnerability management is no longer a nice-to-have but rather a business-critical requirement for any organization running web applications or interactive websites. These public-facing assets are common attack vectors for malicious actors seeking unauthorized access to systems and data.
In the old days of monolithic on-premise applications, vulnerability scanners were deployed primarily in the production environment as infrastructure watchdogs that alerted to runtime threats. This paradigm became obsolete with the emergence of cloud-native applications that leverage modern cloud-based infrastructure's powerful scalability and agility. As applications and the tools to secure them become more complex, solutions like ASPM are emerging to bring together the different data streams and enable risk-based prioritization and remediation.
Today’s highly automated CI/CD pipelines cannot tolerate security testing bottlenecks. The detection and remediation of vulnerabilities must keep up with the frenetic pace of mature DevOps practices.
Yet another challenge to legacy security paradigms is the highly distributed architecture of cloud-native applications based on dynamic components such as open-source libraries, serverless functions, infrastructure as code (IaC), and containers. In short, cloud-native applications require a new cloud-native application security paradigm: ensuring that vulnerabilities are detected and fixed during development with a holistic approach that makes security an integral part of the software development life cycle (SDLC).
Is there a free vulnerability scanner?
There are open-source vulnerability scanners that do not charge a licensing fee. Almost every commercial vulnerability scanner also offers a community edition that is free and delivers a basic set of vulnerability scanning features. Learn more about Snyk’s developer-first Cloud Native Application Security solution.
Snyk Vulnerability Scanning
Snyk’s vulnerability scanning solutions are designed to integrate seamlessly into development workflows, enabling teams to identify and address security risks early in the software development lifecycle. Snyk helps teams uncover vulnerabilities across their entire application stack and provides actionable remediation guidance, allowing teams to resolve issues efficiently without disrupting productivity.
Snyk Open Source: Identifies vulnerabilities in open-source dependencies and provides actionable remediation advice, helping developers maintain secure libraries and frameworks.
Snyk Code: Detects security issues and quality flaws in proprietary code during development, integrating directly into IDEs and CI/CD pipelines.
Snyk Container: Scans container images for vulnerabilities in base images, packages, and configurations, ensuring secure containerized applications.
Snyk Infrastructure as Code (IaC): Identifies misconfigurations in cloud and infrastructure-as-code files, preventing potential security risks before deployment.
Explore the state of open source security
Understand current trends and approaches to open source software and supply chain security.